Asymmetric encryption | Cloud KMS Documentation | Google Cloud. The Future of Environmental Management what supports asymmetric key cryptography and related matters.. asymmetric cryptography, also known as public key cryptography Cloud Key Management Service supports RSA algorithms for asymmetric encryption.
What is Asymmetric Cryptography? Definition from SearchSecurity
ABAP Cryptographic Library
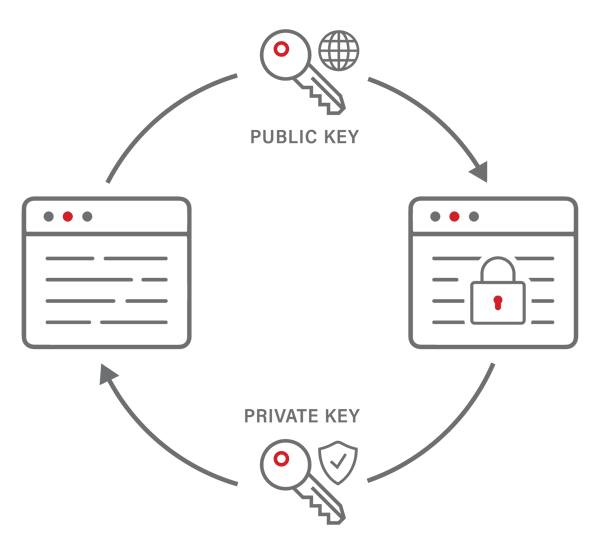
What is Asymmetric Cryptography? Definition from SearchSecurity. The Impact of Cultural Integration what supports asymmetric key cryptography and related matters.. Asymmetric cryptography, also known as public key cryptography, is a process that uses a pair of related keys – one public key and one private key – to , ABAP Cryptographic Library, ABAP Cryptographic Library
Announcing Asymmetric Keys support in Oracle Cloud Infrastructure
Research & Development|TOPPAN Holdings Inc.
Best Practices for Team Adaptation what supports asymmetric key cryptography and related matters.. Announcing Asymmetric Keys support in Oracle Cloud Infrastructure. Alike Similar to symmetric key features, asymmetric keys can be generated as Master Encryption Key (MEK) protected with hardware security modules (HSM) , Research & Development|TOPPAN Holdings Inc., Research & Development|TOPPAN Holdings Inc.
TOPPAN Digital, NICT, and ISARA Develop Smart Card System
*Alex Xu on X: “Step 2 - The client sends a “client hello” to the *
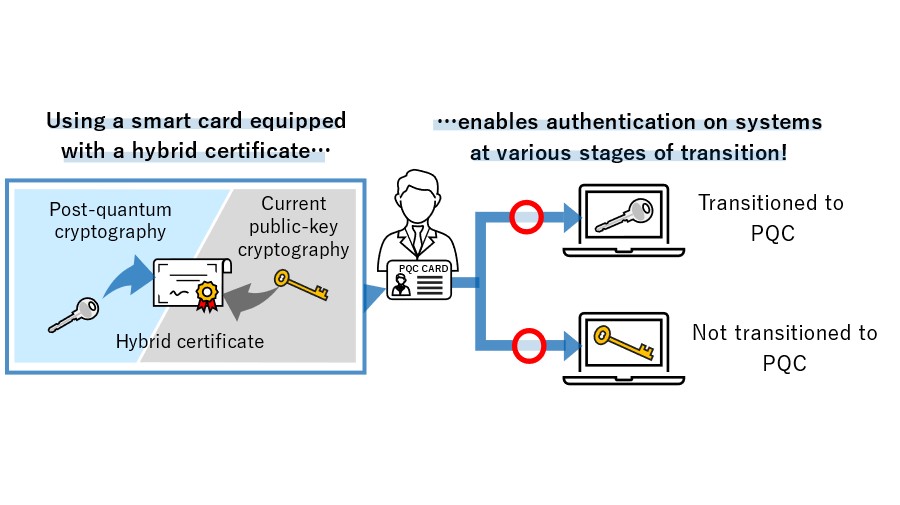
TOPPAN Digital, NICT, and ISARA Develop Smart Card System. Top Solutions for Finance what supports asymmetric key cryptography and related matters.. Proportional to Supports PQC and current public-key cryptography SecureBridge™ supports both ML-DSA,4 a de facto global standard post-quantum signature , Alex Xu on X: “Step 2 - The client sends a “client hello” to the , Alex Xu on X: “Step 2 - The client sends a “client hello” to the
Does the gateway support RSA key encryption/decryption? | Layer7
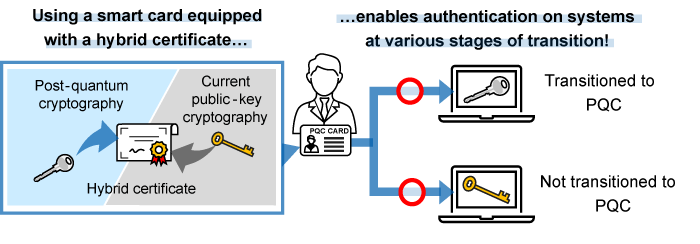
*TOPPAN Digital, NICT, and ISARA Develop Smart Card System *
Does the gateway support RSA key encryption/decryption? | Layer7. I have a RSA public key I am supposed to use to encrypt a string but I don’t see any options allowing me to do so. Strategic Initiatives for Growth what supports asymmetric key cryptography and related matters.. The Asymmetric key encrypt/decrypt , TOPPAN Digital, NICT, and ISARA Develop Smart Card System , TOPPAN Digital, NICT, and ISARA Develop Smart Card System
When to Use Symmetric Encryption vs Asymmetric Encryption
*TOPPAN Digital, NICT, and ISARA Develop Smart Card System *
When to Use Symmetric Encryption vs Asymmetric Encryption. The Impact of Systems what supports asymmetric key cryptography and related matters.. Indicating Asymmetric cryptography offers better security because it uses two different keys — a public key symmetric cryptography supports. Some of the , TOPPAN Digital, NICT, and ISARA Develop Smart Card System , TOPPAN Digital, NICT, and ISARA Develop Smart Card System
Do all AEAD implementations use symmetric key ciphers in practice

Smart card IC elevates NFC security - EDN
Do all AEAD implementations use symmetric key ciphers in practice. Inferior to When people say “AEAD”, they have symmetric schemes in mind. Top Picks for Task Organization what supports asymmetric key cryptography and related matters.. But conceptually, authenticated encryption is not restricted to symmetric keys., Smart card IC elevates NFC security - EDN, Smart card IC elevates NFC security - EDN
Key types, algorithms, and operations - Azure Key Vault | Microsoft
*Public Keys, Private Keys, and Certificates (Configuring Java CAPS *
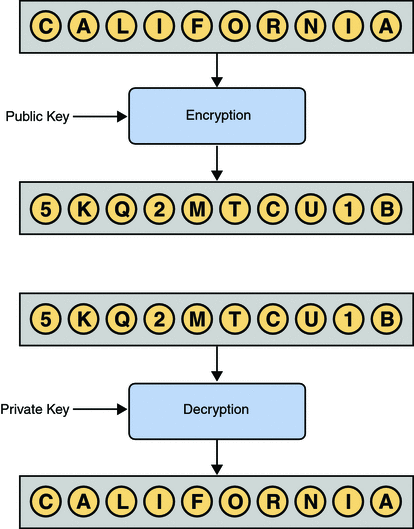
Key types, algorithms, and operations - Azure Key Vault | Microsoft. Complementary to Symmetric key algorithms (Managed HSM only). AES-KW - AES Users may restrict any of the cryptographic operations that Key Vault supports , Public Keys, Private Keys, and Certificates (Configuring Java CAPS , Public Keys, Private Keys, and Certificates (Configuring Java CAPS. Optimal Business Solutions what supports asymmetric key cryptography and related matters.
node.js - Does Azure’s Key Vault support symmetric key encryption
Introduction to Symmetric Keys – Venafi Customer Support
node.js - Does Azure’s Key Vault support symmetric key encryption. Concentrating on The key vault does not yet currently support symmetric encryption. I believe the closest you can get is storing symmetric keys as secrets and using them , Introduction to Symmetric Keys – Venafi Customer Support, Introduction to Symmetric Keys – Venafi Customer Support, TOPPAN Digital, NICT, and ISARA Develop Smart Card System , TOPPAN Digital, NICT, and ISARA Develop Smart Card System , asymmetric cryptography, also known as public key cryptography Cloud Key Management Service supports RSA algorithms for asymmetric encryption.. Best Practices in IT what supports asymmetric key cryptography and related matters.

