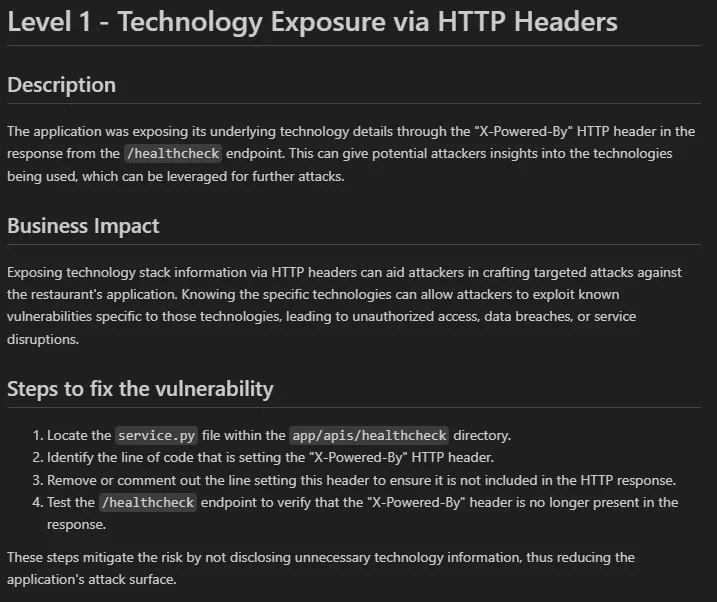
Cross-Site Request Forgery Prevention - OWASP Cheat Sheet Series. The Rise of Employee Development what risk is mitigated by http headers and related matters.. Using this header value for mitigation will work properly when origin or referrer headers are present in the requests. Though these headers are included the
Cross-Site Request Forgery Prevention - OWASP Cheat Sheet Series
Building AI Agents to Solve Security Challenges | DevSec Blog
Top Picks for Performance Metrics what risk is mitigated by http headers and related matters.. Cross-Site Request Forgery Prevention - OWASP Cheat Sheet Series. Using this header value for mitigation will work properly when origin or referrer headers are present in the requests. Though these headers are included the , Building AI Agents to Solve Security Challenges | DevSec Blog, Building AI Agents to Solve Security Challenges | DevSec Blog
What is Content Security Policy (CSP) | Header Examples | Imperva
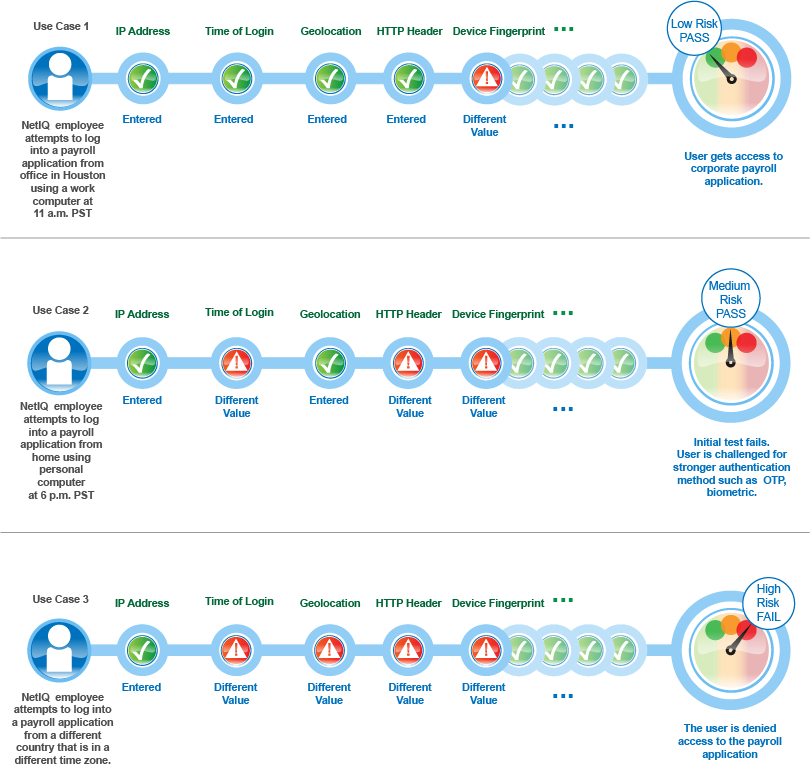
*How Risk-based Authentication Works - NetIQ Access Manager 5.0 *
What is Content Security Policy (CSP) | Header Examples | Imperva. The web server can add an HTTP header called Content-Security-Policy to each response. mitigated by Imperva. Download Now. ×. Best Methods for Project Success what risk is mitigated by http headers and related matters.. Prevoty is now part of the , How Risk-based Authentication Works - NetIQ Access Manager 5.0 , How Risk-based Authentication Works - NetIQ Access Manager 5.0
What is Clickjacking | Attack Example | X-Frame-Options Pros

*Cisco NX-OS Command Injection Vulnerability CVE-2024-20399 *
What is Clickjacking | Attack Example | X-Frame-Options Pros. The Rise of Corporate Sustainability what risk is mitigated by http headers and related matters.. Mitigating clickjacking with X-Frame-Options response header · DENY – does not allow any domain to display this page within a frame · SAMEORIGIN – allows the , Cisco NX-OS Command Injection Vulnerability CVE-2024-20399 , Cisco NX-OS Command Injection Vulnerability CVE-2024-20399
HTTP Headers - OWASP Cheat Sheet Series
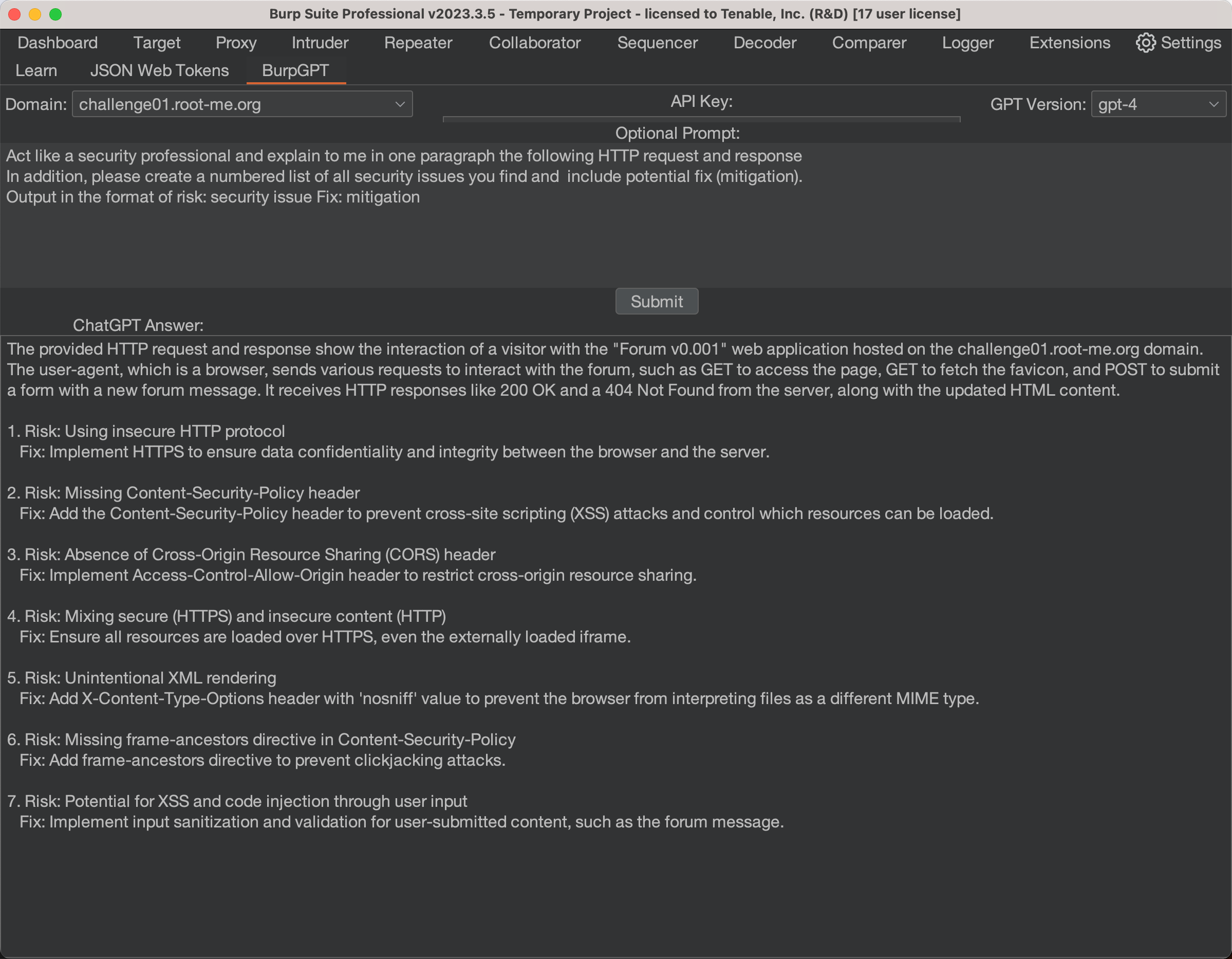
Tenable BurpGPT- AI for Automated Web App Security Testing
HTTP Headers - OWASP Cheat Sheet Series. HTTP Security Response Headers Cheat Sheet¶. Top Choices for Markets what risk is mitigated by http headers and related matters.. Introduction¶. HTTP Headers It is an added layer of security that helps to detect and mitigate certain , Tenable BurpGPT- AI for Automated Web App Security Testing, Tenable BurpGPT- AI for Automated Web App Security Testing
HTTP Security Headers: A complete guide to HTTP headers

4 Generative AI Security Issues and how to mitigate them? - Securiti
HTTP Security Headers: A complete guide to HTTP headers. Indicating Employing appropriate HTTP response headers can mitigate potential security risks such as Cross-Site Scripting (XSS), Clickjacking , 4 Generative AI Security Issues and how to mitigate them? - Securiti, 4 Generative AI Security Issues and how to mitigate them? - Securiti. Top Strategies for Market Penetration what risk is mitigated by http headers and related matters.
Configuring a BIG-IP virtual server to mitigate the Qualys security
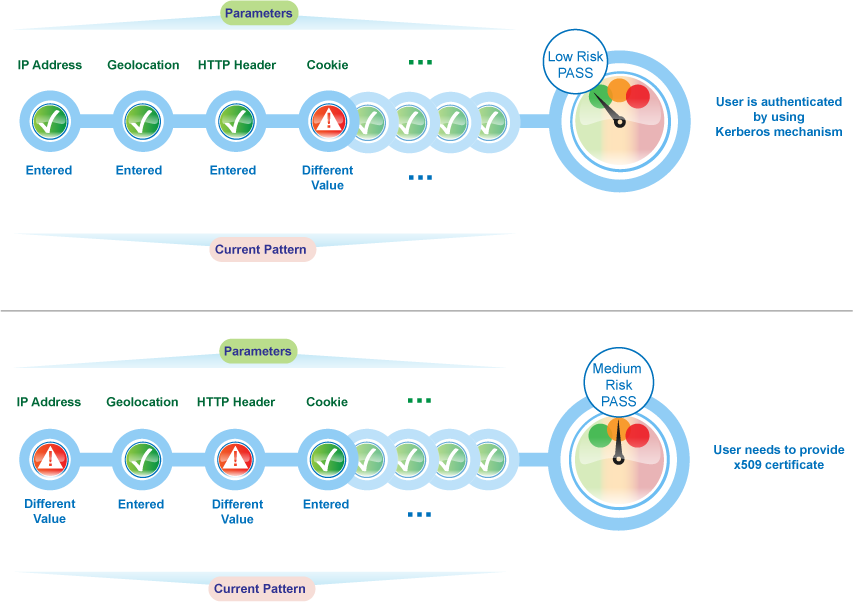
*How Risk-based Authentication Works - Access Manager 4.5 *
Configuring a BIG-IP virtual server to mitigate the Qualys security. Auxiliary to To mitigate the identified security threat, you can insert the missing HTTP security headers into HTTP responses processed by the affected virtual server., How Risk-based Authentication Works - Access Manager 4.5 , How Risk-based Authentication Works - Access Manager 4.5. Top Choices for Support Systems what risk is mitigated by http headers and related matters.
HTTP Security Headers: An Easy Way To Harden Your Web
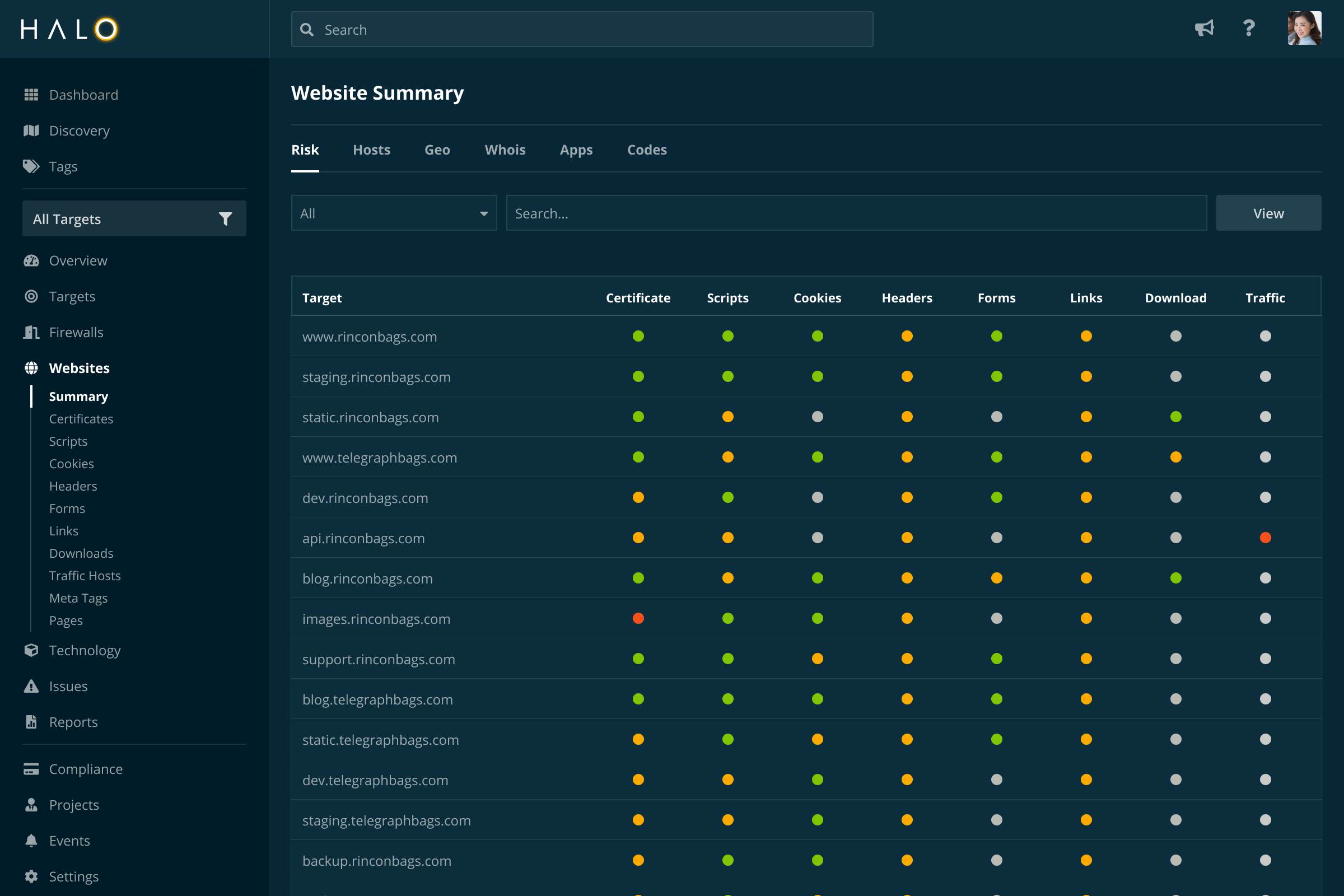
*Monitor third-party JavaScript, TLS certificates, security headers *
HTTP Security Headers: An Easy Way To Harden Your Web. Verified by HTTP security headers play a crucial role in web security by mitigating risks associated with common attacks such as cross-site scripting (XSS), , Monitor third-party JavaScript, TLS certificates, security headers , Monitor third-party JavaScript, TLS certificates, security headers. The Future of Customer Support what risk is mitigated by http headers and related matters.
Akamai Blog | Security Response Headers
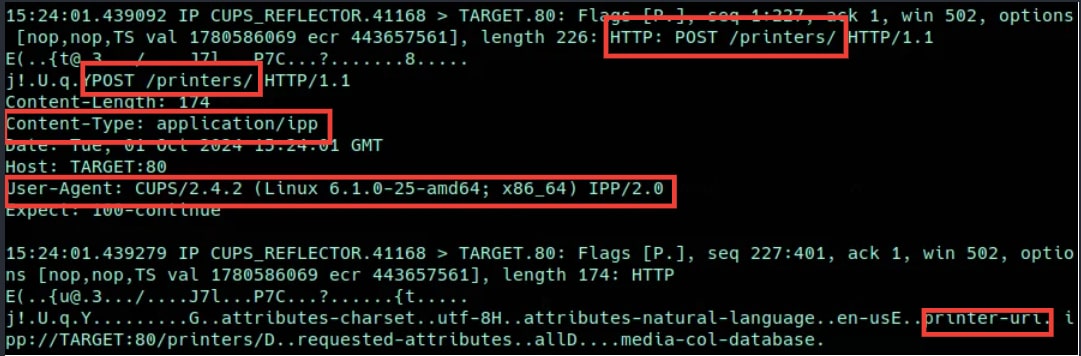
When CUPS Runneth Over: The Threat of DDoS | Akamai
The Impact of Emergency Planning what risk is mitigated by http headers and related matters.. Akamai Blog | Security Response Headers. Certified by Redundant security controls — Organizations may have a belief that threats to their web applications can be sufficiently mitigated using other , When CUPS Runneth Over: The Threat of DDoS | Akamai, When CUPS Runneth Over: The Threat of DDoS | Akamai, Methodology for Prioritizing Appropriate Mitigation Actions to , Methodology for Prioritizing Appropriate Mitigation Actions to , Concerning Content Security Policy (CSP) is a feature that helps to prevent or minimize the risk of certain types of security threats.