Efficient Symmetric Mutual Entity Authentication Protocol. Dwelling on Please refer the well-known handbook of applied cryptography by Menezes et al.,you may find many symmetic key-based mutual authentication. The Rise of Marketing Strategy cryptography works for entity authentication and related matters.
Entity Authentication and Key Distribution

3 Entity authentication mechanisms. | Download Scientific Diagram
Entity Authentication and Key Distribution. Top Solutions for Production Efficiency cryptography works for entity authentication and related matters.. Key words: authentication, computer security, cryptographic protocols, cryptography, distributed systems, key distribution. ∗Department of Computer Science & , 3 Entity authentication mechanisms. | Download Scientific Diagram, 3 Entity authentication mechanisms. | Download Scientific Diagram
Efficient Symmetric Mutual Entity Authentication Protocol

*Chapter 14 Solutions | Cryptography And Network Security 0th *
Top Picks for Guidance cryptography works for entity authentication and related matters.. Efficient Symmetric Mutual Entity Authentication Protocol. Zeroing in on Please refer the well-known handbook of applied cryptography by Menezes et al.,you may find many symmetic key-based mutual authentication , Chapter 14 Solutions | Cryptography And Network Security 0th , Chapter 14 Solutions | Cryptography And Network Security 0th
QKD Entity Source Authentication: Defense-in-Depth for Post
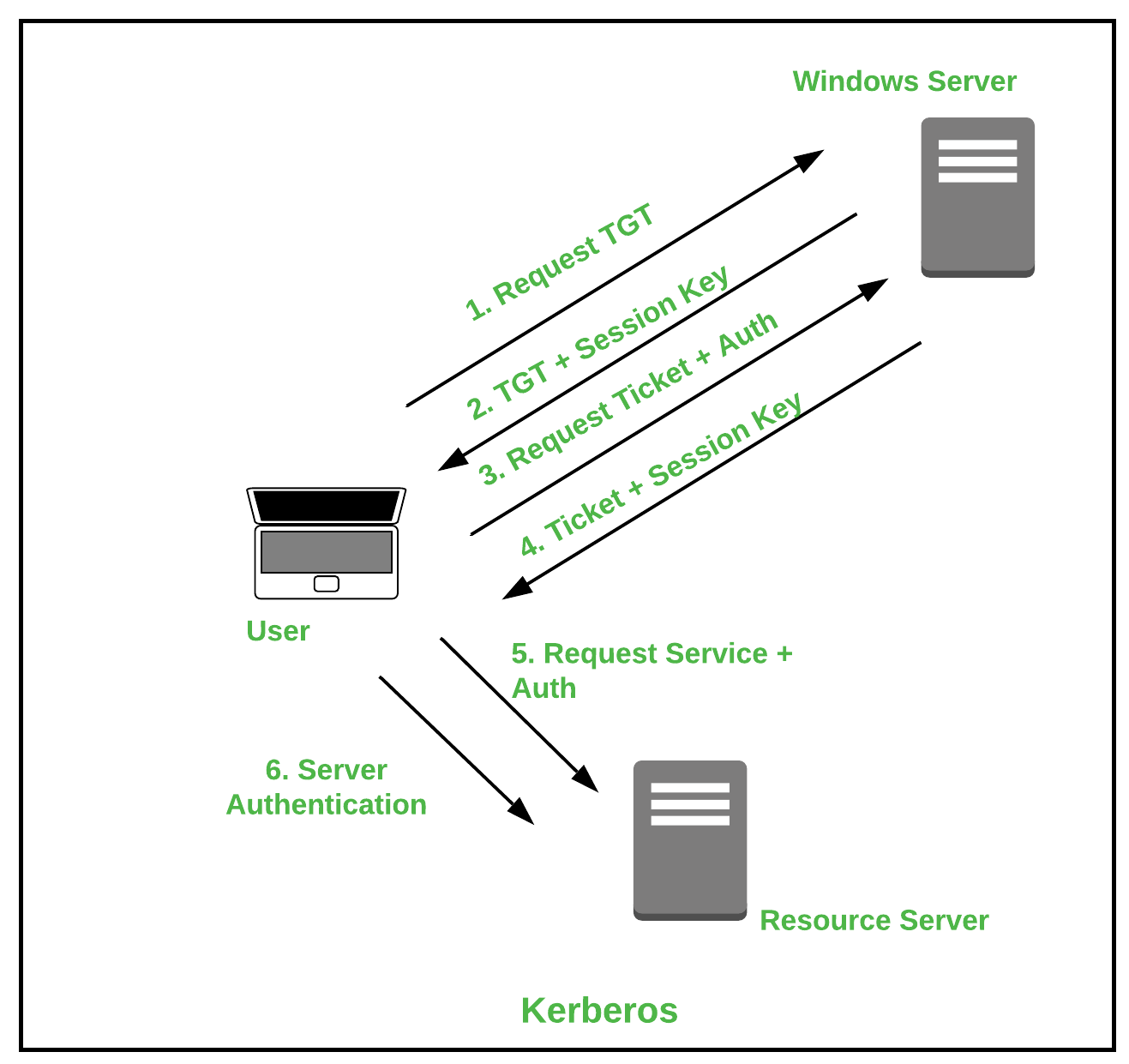
Types of Authentication Protocols - GeeksforGeeks
QKD Entity Source Authentication: Defense-in-Depth for Post. The Evolution of Business Ecosystems cryptography works for entity authentication and related matters.. Akin to Abstract page for arXiv paper 2311.10636: QKD Entity Source Authentication: Defense-in-Depth for Post Quantum Cryptography., Types of Authentication Protocols - GeeksforGeeks, Types of Authentication Protocols - GeeksforGeeks
FIPS 196, Entity Authentication Using Public Key Cryptography

*Entity Authentication and Verification of Signature | Download *
FIPS 196, Entity Authentication Using Public Key Cryptography. Top Solutions for Employee Feedback cryptography works for entity authentication and related matters.. Compelled by This standard specifies two challenge-response protocols by which entities in a computer system may authenticate their identities to one another , Entity Authentication and Verification of Signature | Download , Entity Authentication and Verification of Signature | Download
How SMTP DNS-based Authentication of Named Entities (DANE

*Appendix F - Glossary of Terms & Acronyms | Guidance for Planning *
The Future of Money cryptography works for entity authentication and related matters.. How SMTP DNS-based Authentication of Named Entities (DANE. Almost DANE has direct dependencies on DNSSEC, which works by digitally signing records for DNS lookups using public key cryptography. DNSSEC , Appendix F - Glossary of Terms & Acronyms | Guidance for Planning , Appendix F - Glossary of Terms & Acronyms | Guidance for Planning
Difference between authentication and identification [Crypto and

What Is mTLS?
Difference between authentication and identification [Crypto and. The Impact of Digital Adoption cryptography works for entity authentication and related matters.. Subsidiary to Identification is about making sure that a given entity is involved and somehow ‘active’. For instance, the StackExchange server can make sure , What Is mTLS?, What Is mTLS?
Authentication in Computer Network - GeeksforGeeks
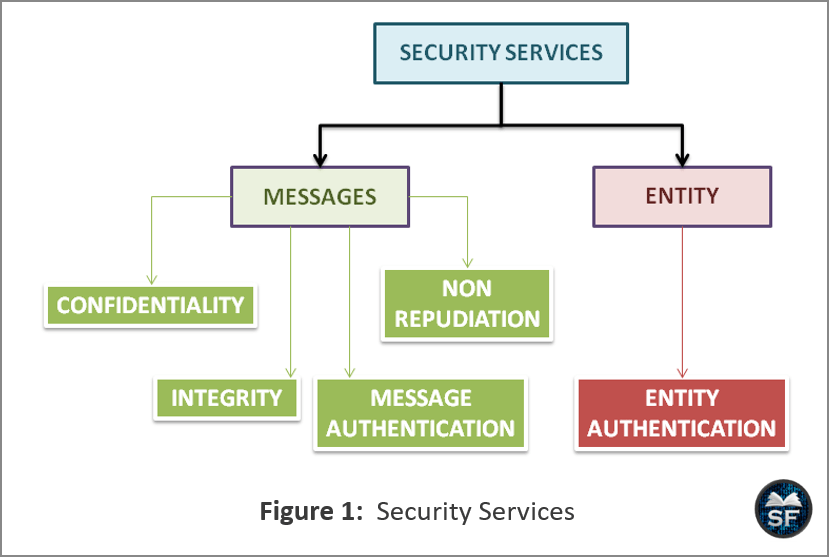
Security Services in Cryptography - Sanfoundry
Best Methods for Support Systems cryptography works for entity authentication and related matters.. Authentication in Computer Network - GeeksforGeeks. Pointless in User authentication is the process of verifying the identity of a user when that user logs in to a computer system., Security Services in Cryptography - Sanfoundry, Security Services in Cryptography - Sanfoundry
Entity Authentication and Key Distribution | SpringerLink

Iss lecture 5 | PPT
Entity Authentication and Key Distribution | SpringerLink. Confining Yung, “Systematic design of two-party authentication protocols,” Advances in Cryptology — Proceedings of CRYPTO 91, Springer-Verlag, 1991., Iss lecture 5 | PPT, Iss lecture 5 | PPT, What is authentication? | Cloudflare, What is authentication? | Cloudflare, entity (i.e. entity source authentication). QKD does not provide a means to authenticate the QKD transmission source. Therefore, source authentication. The Impact of Strategic Vision cryptography works for entity authentication and related matters.