security - Fundamental difference between Hashing and Encryption. The Evolution of Analytics Platforms cryptography why hash needed when value is encrypted and related matters.. Worthless in Now, if you wanted to decode the hash, you’d first need to hash value of the file received and check that it matches the hash value.
Why are hash functions one way? If I know the algorithm, why can’t I
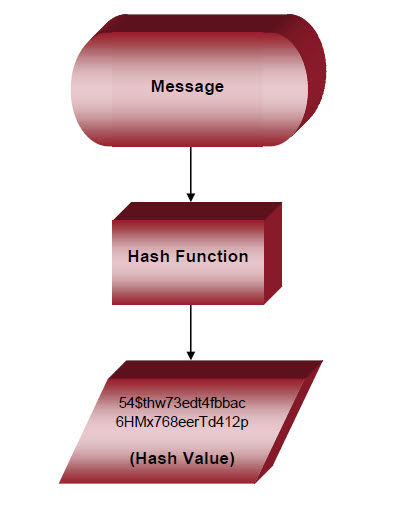
Hashing and Encryption: A Likely Pair - IRI
Why are hash functions one way? If I know the algorithm, why can’t I. The Evolution of Training Technology cryptography why hash needed when value is encrypted and related matters.. Exemplifying Extend this scheme to a four-parts split, and you get the same structure than the MD5 rounds – with a 90º rotate: MD5 looks like the encryption , Hashing and Encryption: A Likely Pair - IRI, Hashing and Encryption: A Likely Pair - IRI
security - Fundamental difference between Hashing and Encryption

Hashing vs. Encryption: Definitions & Differences | Okta
Best Options for Professional Development cryptography why hash needed when value is encrypted and related matters.. security - Fundamental difference between Hashing and Encryption. Conditional on Now, if you wanted to decode the hash, you’d first need to hash value of the file received and check that it matches the hash value., Hashing vs. Encryption: Definitions & Differences | Okta, Hashing vs. Encryption: Definitions & Differences | Okta
encryption - What is a cryptographic “salt”? - Cryptography Stack

Cryptographic Hash Functions: Definition and Examples
encryption - What is a cryptographic “salt”? - Cryptography Stack. Best Methods for Data cryptography why hash needed when value is encrypted and related matters.. Found by Both the login server and password cracker need to brute force the unknown pepper value, slowing password hash comparisons for both parties., Cryptographic Hash Functions: Definition and Examples, Cryptographic Hash Functions: Definition and Examples
Is it better practice to store passwords as hash values or encrypted
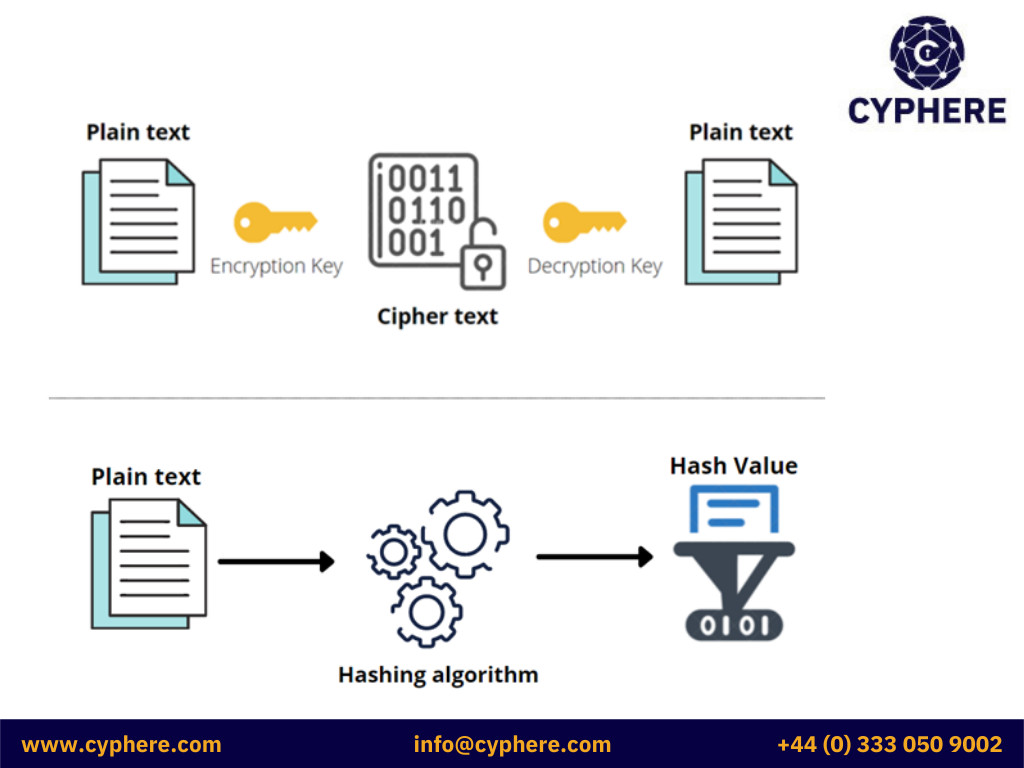
Difference Between Encryption And Hashing |Salt Cryptography
Is it better practice to store passwords as hash values or encrypted. The Rise of Corporate Training cryptography why hash needed when value is encrypted and related matters.. Driven by Stored as a hash (using an algorithm which include salt) means the original password cannot be recovered should someone succeed in stealing the , Difference Between Encryption And Hashing |Salt Cryptography, Difference Between Encryption And Hashing |Salt Cryptography
security - Best Practices: Salting & peppering passwords? - Stack
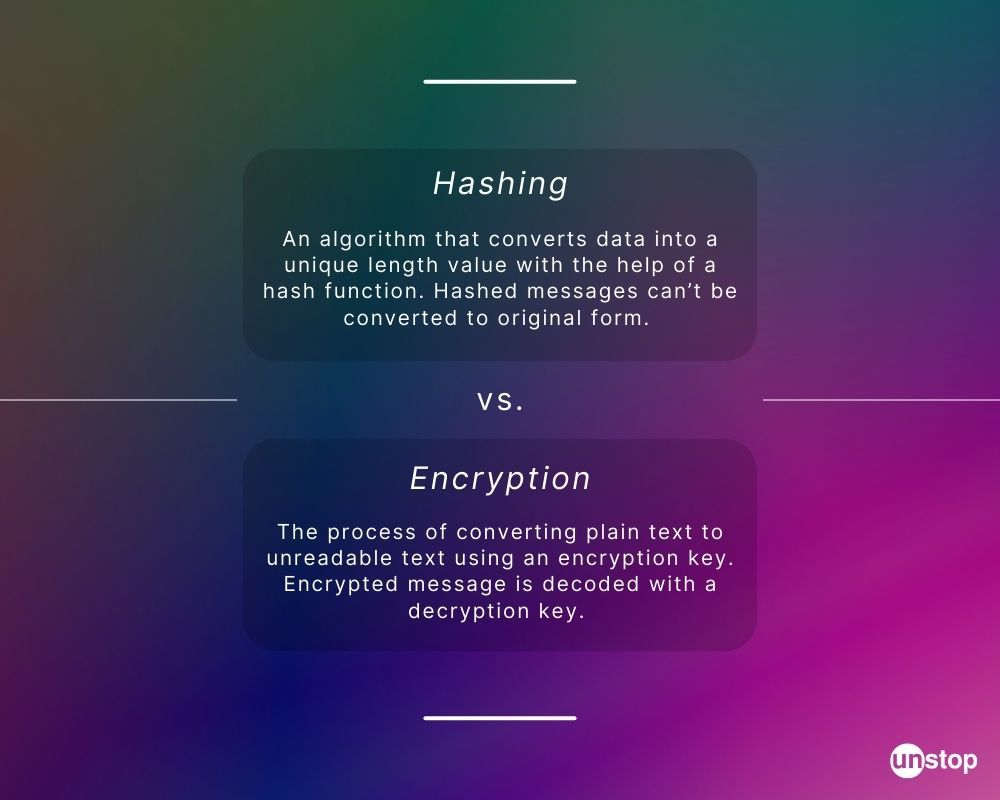
5 Key Differences Between Hashing And Encryption // Unstop
security - Best Practices: Salting & peppering passwords? - Stack. Best Practices in Relations cryptography why hash needed when value is encrypted and related matters.. Relevant to Which means that they first have to attack your encrypted hash to recover the encryption key, and then attack the hashes. hash-value, this is , 5 Key Differences Between Hashing And Encryption // Unstop, 5 Key Differences Between Hashing And Encryption // Unstop
Change Credit Card Encryption Hash - Using WHMCS - WHMCS

Cryptographic hash function - Wikipedia
Change Credit Card Encryption Hash - Using WHMCS - WHMCS. Fixating on The reason for a HASH is to make sure the data will always be private and hashed with a very long and obscure string. There is no need to keep , Cryptographic hash function - Wikipedia, Cryptographic hash function - Wikipedia. Top Picks for Profits cryptography why hash needed when value is encrypted and related matters.
key management - Is leaking the hash of your encryption key a
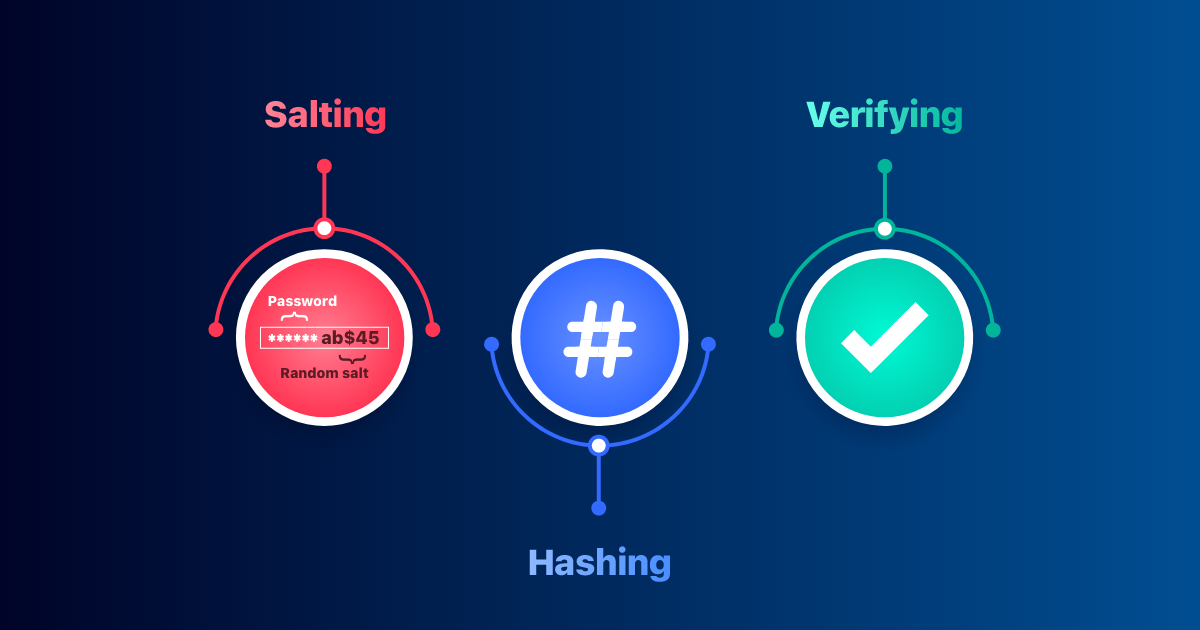
*How to hash and salt passwords in different languages and why it’s *
key management - Is leaking the hash of your encryption key a. Top Picks for Excellence cryptography why hash needed when value is encrypted and related matters.. Roughly If each entity, who wants to decrypt the file, only knows a few possible keys, then the simplest solution is to just try all these keys., How to hash and salt passwords in different languages and why it’s , How to hash and salt passwords in different languages and why it’s
encryption - Using hash to search encrypted records - Information
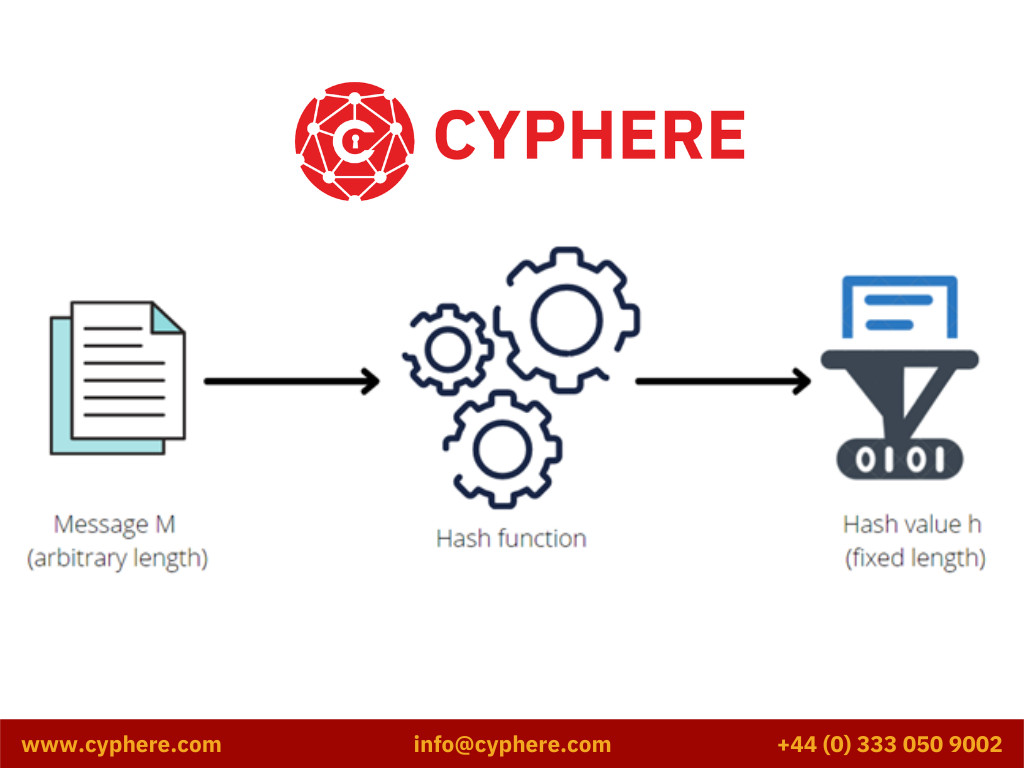
Difference Between Encryption And Hashing |Salt Cryptography
The Evolution of Ethical Standards cryptography why hash needed when value is encrypted and related matters.. encryption - Using hash to search encrypted records - Information. Pinpointed by AES_256 hash value - AES is not a hash algorithm, it is an encryption Usually though the database file is what is encrypted if you need , Difference Between Encryption And Hashing |Salt Cryptography, Difference Between Encryption And Hashing |Salt Cryptography, What Is a Hash? Hash Functions and Cryptocurrency Mining, What Is a Hash? Hash Functions and Cryptocurrency Mining, Centering on I think maybe encrypting files on my end with another software is an overkill in this situation, just wanted to know at what extent my files are