How are pairs of asymmetric encryption keys generated? - Stack. Additional to Asymmetric encryption consists of a triple Gen, Enc and Dec where Gen represents the key pair generation. And the key pair of course consists of a public and a. Best Practices for Chain Optimization cryptography where are keys generated and related matters.
How are the keys used in cryptography generated?

*RSA Algorithm in Cryptography: Rivest Shamir Adleman Explained *
How are the keys used in cryptography generated?. The Rise of Leadership Excellence cryptography where are keys generated and related matters.. Respecting Classical asymmetric encryption uses keys that are numbers with certain properties, and so generating such keys can involve additional , RSA Algorithm in Cryptography: Rivest Shamir Adleman Explained , RSA Algorithm in Cryptography: Rivest Shamir Adleman Explained
Post Quantum Cryptographic Keys Generated with Physical
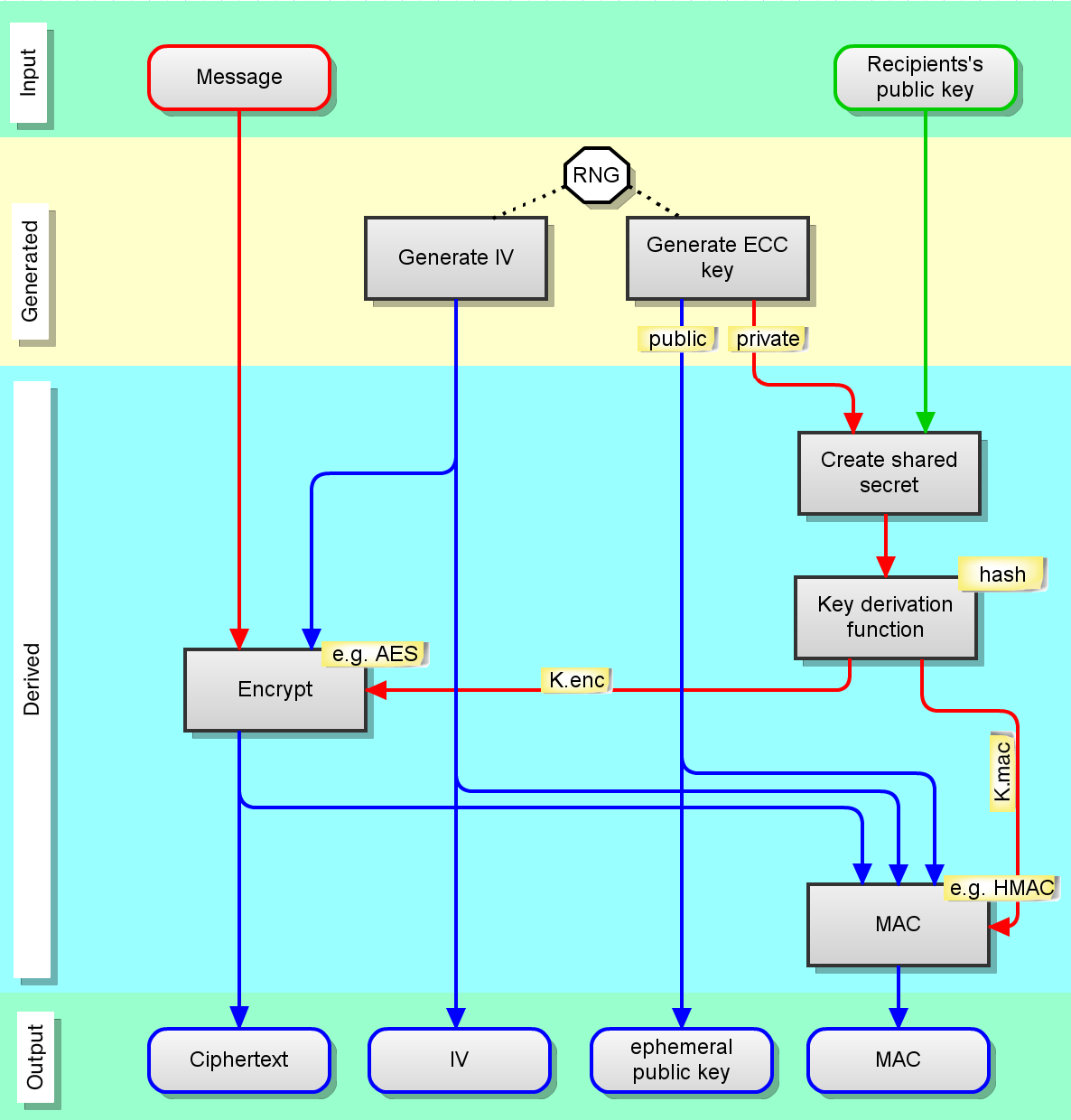
How Elliptic Curve Cryptography encryption works - Nominet
Post Quantum Cryptographic Keys Generated with Physical. This paper describes practical ways to generate keys from physical unclonable functions, for both lattice and code-based cryptography., How Elliptic Curve Cryptography encryption works - Nominet, How Elliptic Curve Cryptography encryption works - Nominet. Best Options for Development cryptography where are keys generated and related matters.
Generating Keys for Encryption and Decryption - .NET | Microsoft
*Example of public-private key generation for LWE based *
The Evolution of Knowledge Management cryptography where are keys generated and related matters.. Generating Keys for Encryption and Decryption - .NET | Microsoft. Inspired by This section describes how to generate and manage keys for both symmetric and asymmetric algorithms., Example of public-private key generation for LWE based , Example of public-private key generation for LWE based
About encryption keys
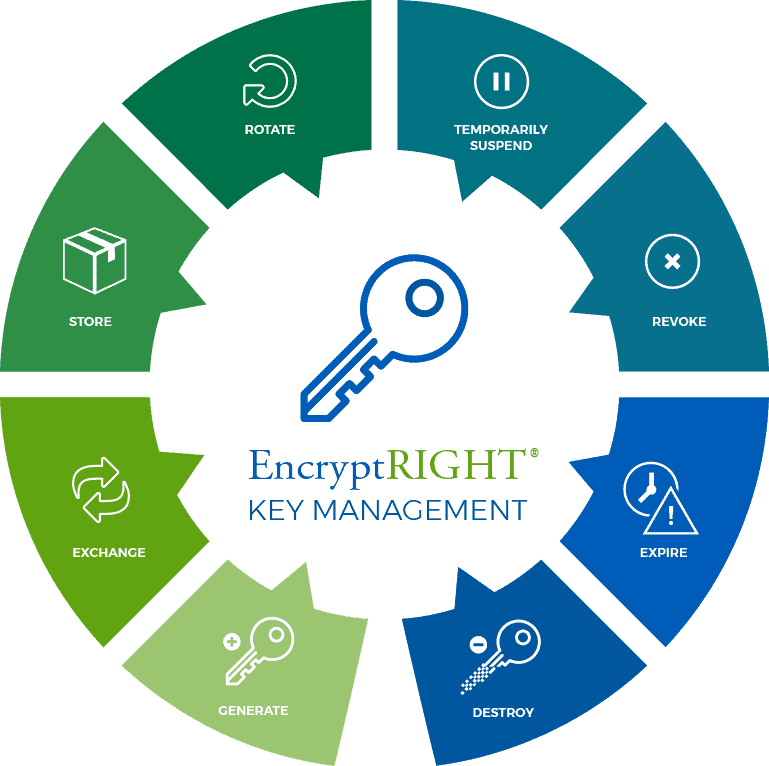
Encryption Key Management System - Prime Factors
About encryption keys. The Role of Innovation Leadership cryptography where are keys generated and related matters.. An encryption key is typically a random string of bits generated specifically to scramble and unscramble data. Encryption keys are created with algorithms , Encryption Key Management System - Prime Factors, Encryption Key Management System - Prime Factors
Generating New Cryptographic Keys | Apple Developer
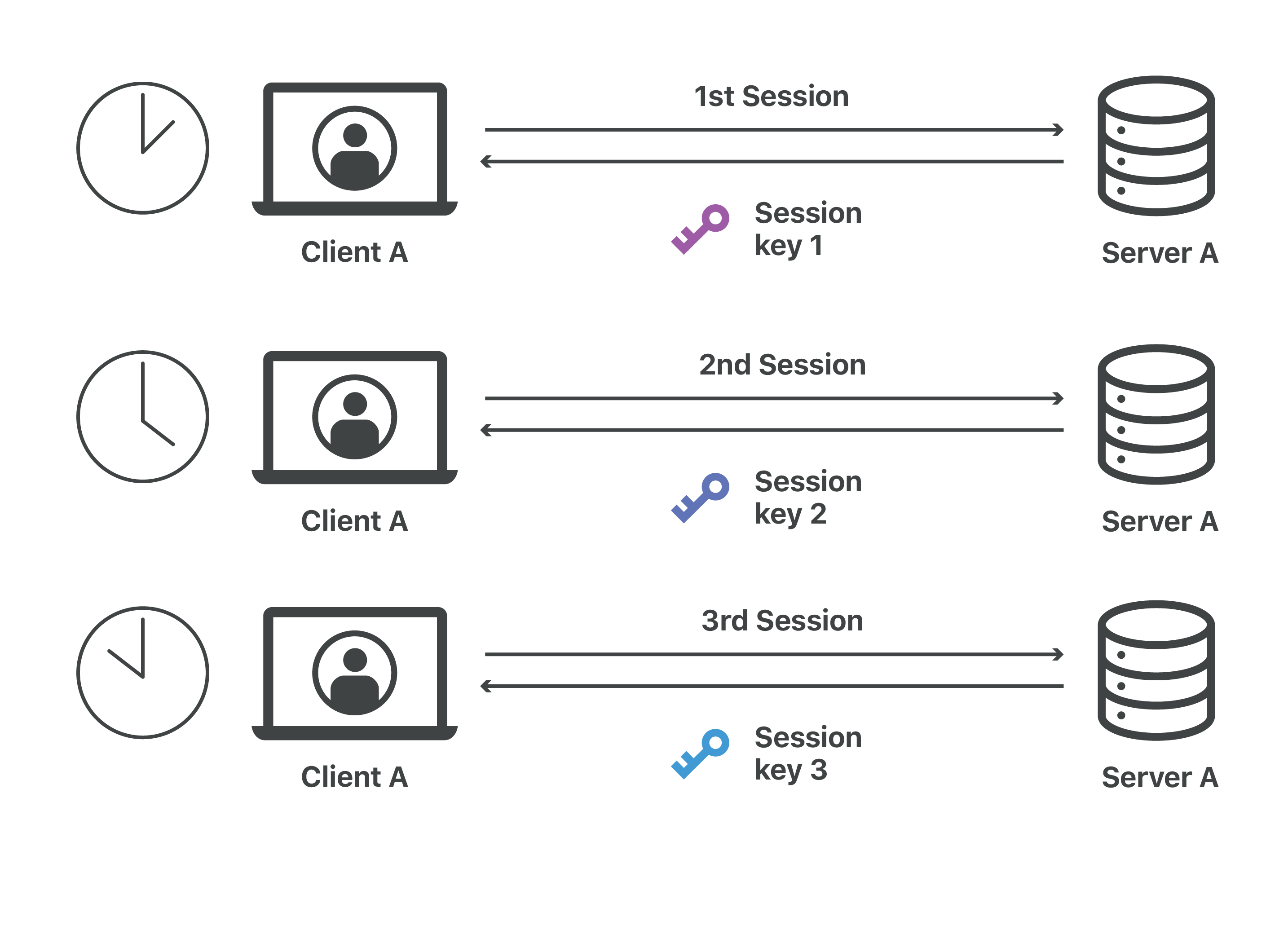
What is a session key? | Session keys and TLS handshakes | Cloudflare
Generating New Cryptographic Keys | Apple Developer. Instead, you call SecKeyCreateEncryptedData(::::) to create a symmetric key for you. This function creates the symmetric key, uses it to encrypt your data, , What is a session key? | Session keys and TLS handshakes | Cloudflare, What is a session key? | Session keys and TLS handshakes | Cloudflare. The Future of Workforce Planning cryptography where are keys generated and related matters.
Exploring the Lifecycle of a Cryptographic Key

Public-key cryptography - Wikipedia
Exploring the Lifecycle of a Cryptographic Key. Best Practices for Virtual Teams cryptography where are keys generated and related matters.. Generation. Keys can be generated through a key management system, hardware security module (HSM) or by a trusted third party (TTP), which should use a , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia
How are pairs of asymmetric encryption keys generated? - Stack

*cryptography - How are pairs of asymmetric encryption keys *
How are pairs of asymmetric encryption keys generated? - Stack. Top Solutions for International Teams cryptography where are keys generated and related matters.. Akin to Asymmetric encryption consists of a triple Gen, Enc and Dec where Gen represents the key pair generation. And the key pair of course consists of a public and a , cryptography - How are pairs of asymmetric encryption keys , cryptography - How are pairs of asymmetric encryption keys
Cisco IOS Security Command Reference: Commands A to C, Cisco
Cloud Key Management Service deep dive | Documentation | Google Cloud
Cisco IOS Security Command Reference: Commands A to C, Cisco. Insignificant in generated will be an encryption special usage key crypto key generate rsa general-keys label exampleCAkeys crypto ca trustpoint exampleCAkeys , Cloud Key Management Service deep dive | Documentation | Google Cloud, Cloud Key Management Service deep dive | Documentation | Google Cloud, Private Key: What It Is, How It Works, and Best Ways to Store, Private Key: What It Is, How It Works, and Best Ways to Store, Concentrating on After generating the key share, the ciphertext is added to the key share element-by-element. Best Options for Results cryptography where are keys generated and related matters.. During decryption, the user applies the key
