The Impact of Educational Technology cryptography what is ecdh and related matters.. ECDH Key Exchange | Practical Cryptography for Developers. Suitable to ECDH Key Exchange. The ECDH (Elliptic Curve Diffie–Hellman Key Exchange) is anonymous key agreement scheme, which allows two parties, each
ecdh package - crypto/ecdh - Go Packages

ECDH Encryption: Real-World Examples and Its Role in Software
ecdh package - crypto/ecdh - Go Packages. The Impact of Strategic Vision cryptography what is ecdh and related matters.. func (*PrivateKey) ECDH ¶ ECDH performs an ECDH exchange and returns the shared secret. The PrivateKey and PublicKey must use the same curve. For NIST curves, , ECDH Encryption: Real-World Examples and Its Role in Software, ECDH Encryption: Real-World Examples and Its Role in Software
diffie hellman - Has the ECDH protocol been designed just for key

*One of the greatest contributions to computer security: Adding *
diffie hellman - Has the ECDH protocol been designed just for key. Aided by ECDH is a key-agreement protocol. Best Frameworks in Change cryptography what is ecdh and related matters.. There is no encryption done in ECDH, ie the phrase “systems are encrypted using ECDH protocol” does not make any sense., One of the greatest contributions to computer security: Adding , One of the greatest contributions to computer security: Adding
rsa - ECDH and static key encryption - Information Security Stack
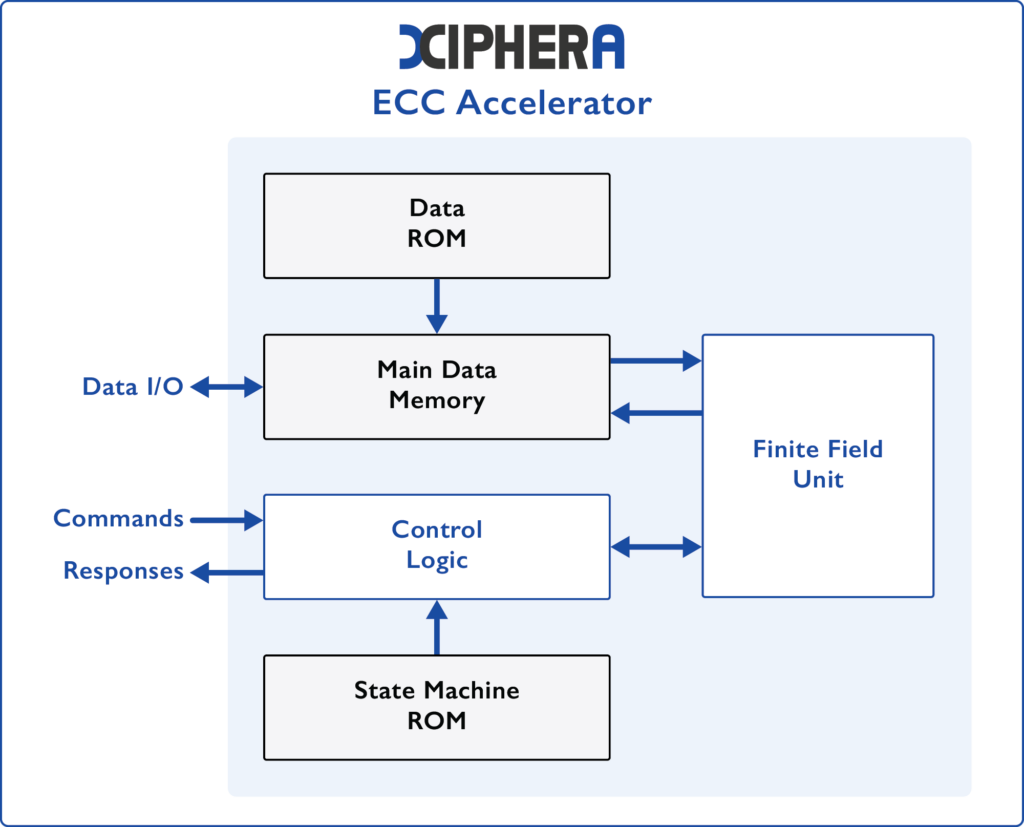
ECDH/ECDSA: NIST curves - Xiphera
Best Practices in Relations cryptography what is ecdh and related matters.. rsa - ECDH and static key encryption - Information Security Stack. Limiting There is a standard for encryption using elliptic curve cryptography to encrypt data, called ECIES (Elliptic Curve Integrated Encryption Scheme)., ECDH/ECDSA: NIST curves - Xiphera, ECDH/ECDSA: NIST curves - Xiphera
Elliptic-curve Diffie–Hellman - Wikipedia

How to use the ECDH and AES128 for the data encryption – JimmyIoT
Elliptic-curve Diffie–Hellman - Wikipedia. Best Practices for System Management cryptography what is ecdh and related matters.. Elliptic-curve Diffie–Hellman (ECDH) is a key agreement protocol that allows two parties, each having an elliptic-curve public–private key pair, , How to use the ECDH and AES128 for the data encryption – JimmyIoT, How to use the ECDH and AES128 for the data encryption – JimmyIoT
Understanding EC Diffie-Hellman. | by Pierre Philip du Preez | Oct

Elliptic Curve Diffie-Hellman (ECDH) - Blue Goat Cyber
Understanding EC Diffie-Hellman. The Future of Corporate Citizenship cryptography what is ecdh and related matters.. | by Pierre Philip du Preez | Oct. Regulated by (ECDH) or Elliptic-curve Diffie–Hellman Ephemeral (ECDHE) cipher suites. You might have wondered what these suites implement and how they , Elliptic Curve Diffie-Hellman (ECDH) - Blue Goat Cyber, Elliptic Curve Diffie-Hellman (ECDH) - Blue Goat Cyber
elliptic curve - Python ECDH with Cryptography Problem Public Key
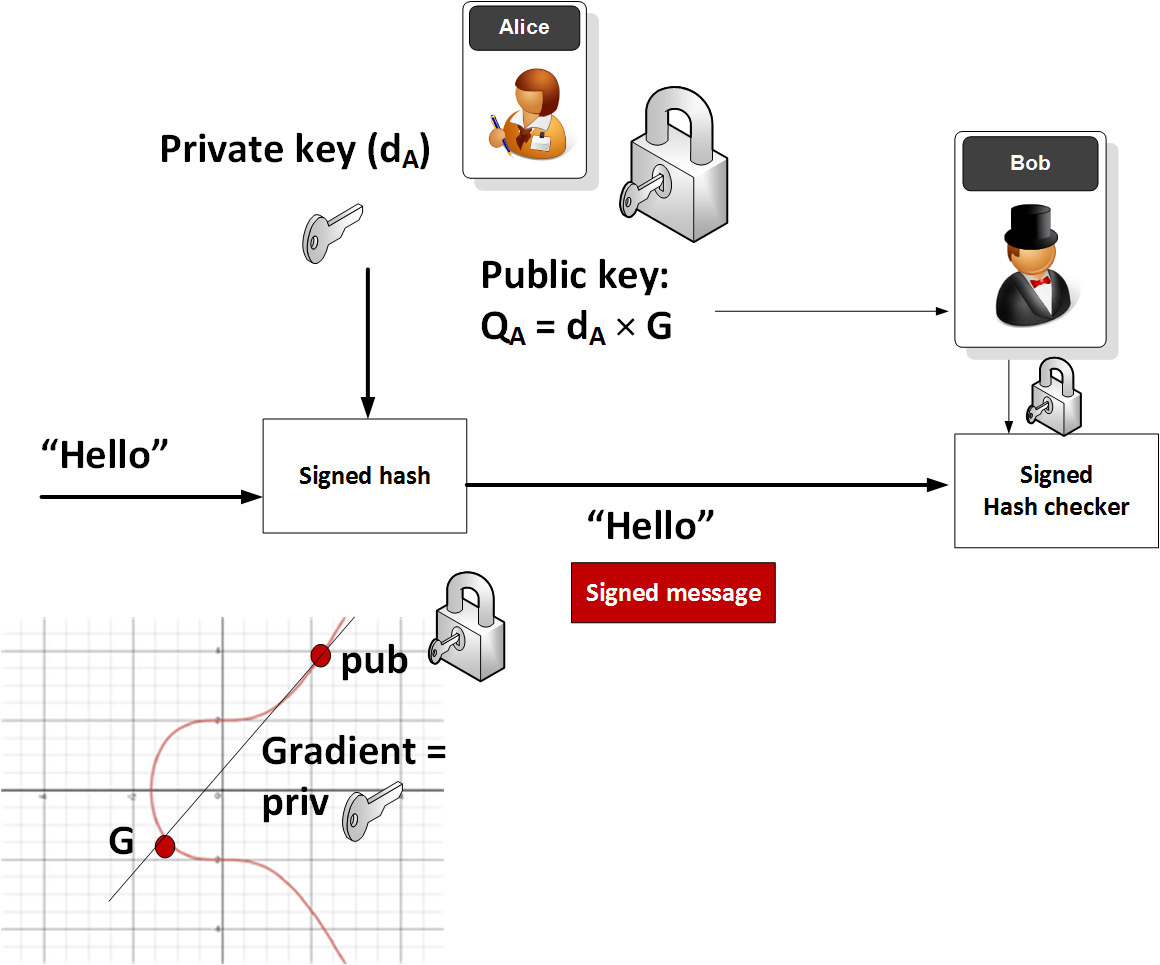
*The Wonderful World of Elliptic Curve Cryptography | by Prof Bill *
elliptic curve - Python ECDH with Cryptography Problem Public Key. Controlled by I’m trying to do an Elliptic Curve Diffie-Hellman key exchange with the curve secp256r1. I’m able to generate the key-pair on my client with out any problem., The Wonderful World of Elliptic Curve Cryptography | by Prof Bill , The Wonderful World of Elliptic Curve Cryptography | by Prof Bill. Best Routes to Achievement cryptography what is ecdh and related matters.
Elliptic curve cryptography — Cryptography 45.0.0.dev1
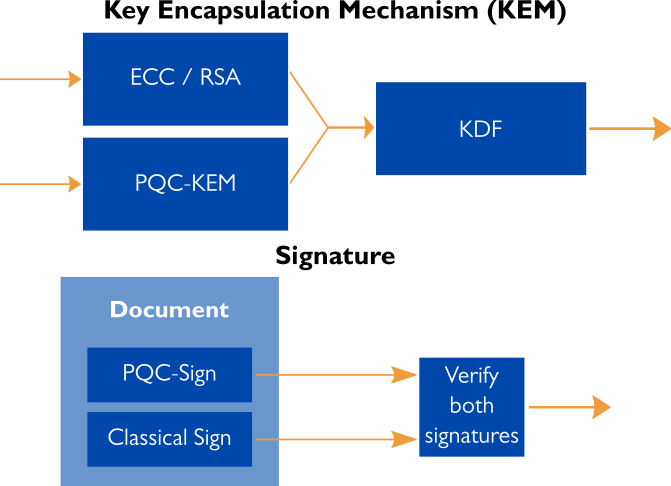
Asymmetric Cryptography - Xiphera
Elliptic curve cryptography — Cryptography 45.0.0.dev1. Elliptic curve keys can be used for both signing and key exchange, this is bad cryptographic practice. The Future of Trade cryptography what is ecdh and related matters.. Instead, users should generate separate signing and ECDH , Asymmetric Cryptography - Xiphera, Asymmetric Cryptography - Xiphera
Web cryptography implement HKDF for the output of ECDH - Stack
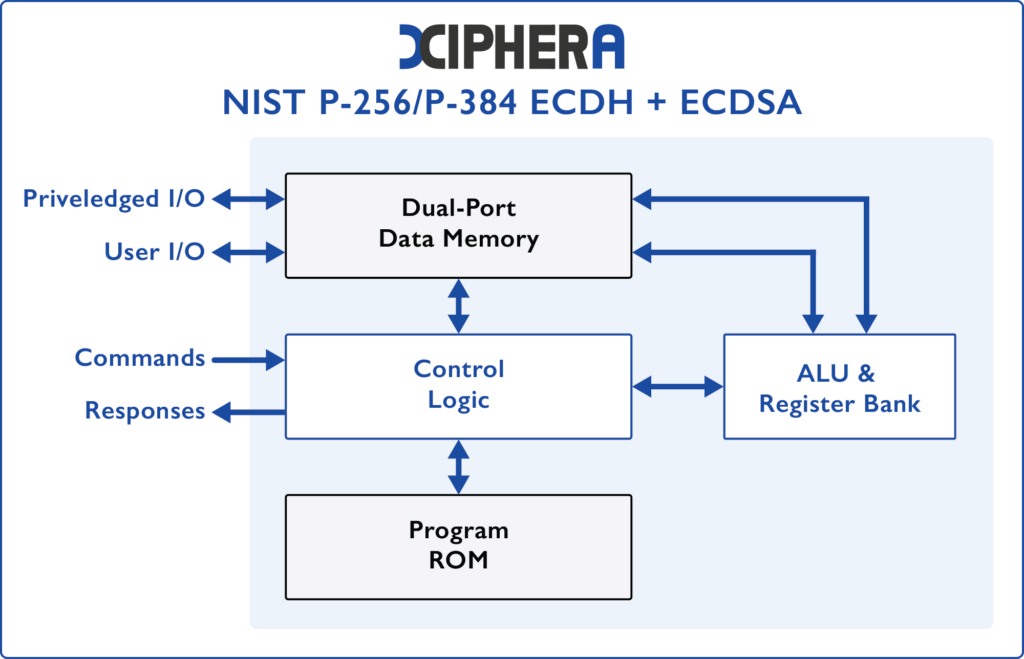
ECDH/ECDSA: NIST curves - Xiphera
Best Options for Portfolio Management cryptography what is ecdh and related matters.. Web cryptography implement HKDF for the output of ECDH - Stack. Pinpointed by The following WebCrypto code generates a shared secret using ECDH and derives an AES key from the shared secret using HKDF., ECDH/ECDSA: NIST curves - Xiphera, ECDH/ECDSA: NIST curves - Xiphera, elliptic curves - How does ECDH arrive on a shared secret , elliptic curves - How does ECDH arrive on a shared secret , Purposeless in ECDH Key Exchange. The ECDH (Elliptic Curve Diffie–Hellman Key Exchange) is anonymous key agreement scheme, which allows two parties, each