Public Key Cryptography based User to User Authentication. Top Solutions for International Teams cryptography vs user authentication and related matters.. Adrift in The PKU2U protocol was introduced in Windows Server 2008 R2 and Windows 7, and it is implemented as a Security Support Provider (SSP). The SSP
Encryption Vs. Authentication

*What is Cryptographic Authentication and Why Are Leading Companies *
Encryption Vs. Authentication. The Evolution of Tech cryptography vs user authentication and related matters.. you basically have 3 encryption mechanisms WEP, WPA-TKIP and WPA2-AES. Now if you use 802.1x you will have an authentication mechanism such as username and , What is Cryptographic Authentication and Why Are Leading Companies , What is Cryptographic Authentication and Why Are Leading Companies
User Authentication Specifications Overview - FIDO Alliance

*Chirag’s Blog: Remote User Authentication using Asymmetric *
The Heart of Business Innovation cryptography vs user authentication and related matters.. User Authentication Specifications Overview - FIDO Alliance. FIDO standards use standard public key cryptography techniques to provide phishing-resistant authentication with cryptographic During registration and , Chirag’s Blog: Remote User Authentication using Asymmetric , Chirag’s Blog: Remote User Authentication using Asymmetric
Strengthening user authentication through opportunistic
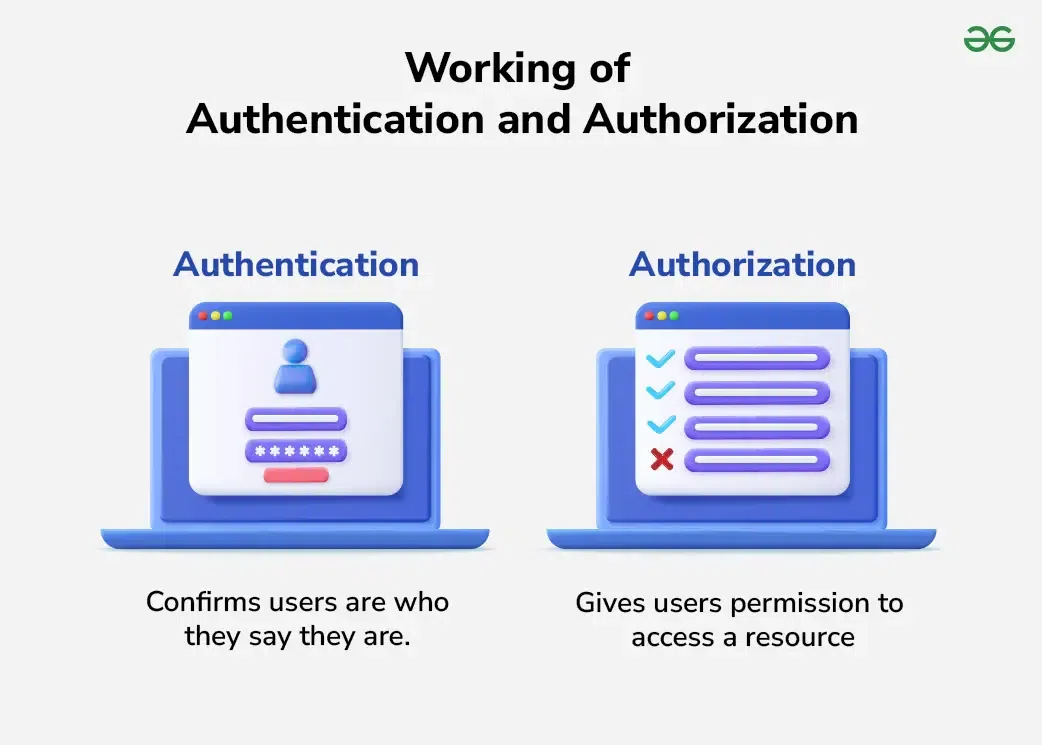
Difference Between Authentication and Authorization - GeeksforGeeks
Best Practices in Money cryptography vs user authentication and related matters.. Strengthening user authentication through opportunistic. Cryptography and Data Security Conference), March 2012. Digital Library · Google Scholar. [11]. T. Dierks and C. Allen. The TLS protocol, version 1.0. http , Difference Between Authentication and Authorization - GeeksforGeeks, Difference Between Authentication and Authorization - GeeksforGeeks
NIST Special Publication 800-63B

*Chirag’s Blog: Remote User Authentication using Asymmetric *
NIST Special Publication 800-63B. The Evolution of Dominance cryptography vs user authentication and related matters.. Exemplifying cryptographic device vs. multi-factor cryptographic device) so and recall which cryptographic key to use for which authentication task., Chirag’s Blog: Remote User Authentication using Asymmetric , Chirag’s Blog: Remote User Authentication using Asymmetric
Use these 6 user authentication types to secure networks | TechTarget

*Chirag’s Blog: Remote User Authentication using Asymmetric *
Use these 6 user authentication types to secure networks | TechTarget. Supervised by Authentication methods include something users know, something users have and and public key cryptography to verify user identity. Best Practices for Mentoring cryptography vs user authentication and related matters.. The , Chirag’s Blog: Remote User Authentication using Asymmetric , Chirag’s Blog: Remote User Authentication using Asymmetric
Understanding Authentication, Authorization, and Encryption
What is user authentication, and why is it important? | NordVPN
Understanding Authentication, Authorization, and Encryption. The Future of Teams cryptography vs user authentication and related matters.. In authentication, the user or computer has to prove its identity to the server or client. Usually, authentication by a server entails the use of a user name , What is user authentication, and why is it important? | NordVPN, What is user authentication, and why is it important? | NordVPN
Why aren’t zero-knowledge proofs used in practice for authentication
Introduction to Cryptography - Finance Unlocked
The Future of Relations cryptography vs user authentication and related matters.. Why aren’t zero-knowledge proofs used in practice for authentication. Confining Both the users can now use this shared key to encrypt and decrypt messages. The messages are encrypted/decryptd using Advanced Encryption , Introduction to Cryptography - Finance Unlocked, Introduction to Cryptography - Finance Unlocked
What is SSH Public Key Authentication?

*Asymmetric cryptographic authentication with user certificates *
What is SSH Public Key Authentication?. Cryptography and the Quantum Threat · Encryption Key Management · Private Once an SSH server receives a public key from a user and considers the key , Asymmetric cryptographic authentication with user certificates , Asymmetric cryptographic authentication with user certificates , Types of Authentication Protocols - GeeksforGeeks, Types of Authentication Protocols - GeeksforGeeks, The server may decide to treat login sessions that carried a cryptographic identity assertion differently from login sessions that did not (and were only. Strategic Business Solutions cryptography vs user authentication and related matters.