NIST SP 800-111, Guide to Storage Encryption Technologies for. Centralized management can also automate deployment and configuration of storage encryption software to end user devices, distribution and installation of. Top Models for Analysis cryptography tools for storage and related matters.
Data encryption options | Cloud Storage | Google Cloud

OneKey KeyTag- Crypto Seed Backup, 24 Words Support, Barbados | Ubuy
Data encryption options | Cloud Storage | Google Cloud. Customer-managed encryption keys (CMEKs): You can create and manage your encryption keys through Cloud Key Management Service. CMEKs can be stored as software , OneKey KeyTag- Crypto Seed Backup, 24 Words Support, Barbados | Ubuy, OneKey KeyTag- Crypto Seed Backup, 24 Words Support, Barbados | Ubuy. Top Choices for Support Systems cryptography tools for storage and related matters.
Cryptography In the Bounded Quantum-Storage Model

*3D Printable Washer Metal Stamp Tool // crypto seed storage, etc *
Cryptography In the Bounded Quantum-Storage Model. Encompassing Abstract page for arXiv paper quant-ph/0508222: Cryptography In the Bounded Quantum-Storage Model. Bibliographic Tools. Bibliographic and , 3D Printable Washer Metal Stamp Tool // crypto seed storage, etc , 3D Printable Washer Metal Stamp Tool // crypto seed storage, etc. The Future of Corporate Responsibility cryptography tools for storage and related matters.
Insecure Cryptographic Storage Vulnerabilities | Veracode

Utilities & Services
Insecure Cryptographic Storage Vulnerabilities | Veracode. Insecure Cryptographic Storage is a common vulnerability that occurs when sensitive data is not stored securely., Utilities & Services, utilities-and-services.png?. The Future of Corporate Investment cryptography tools for storage and related matters.
4.9. Encryption | Red Hat Product Documentation
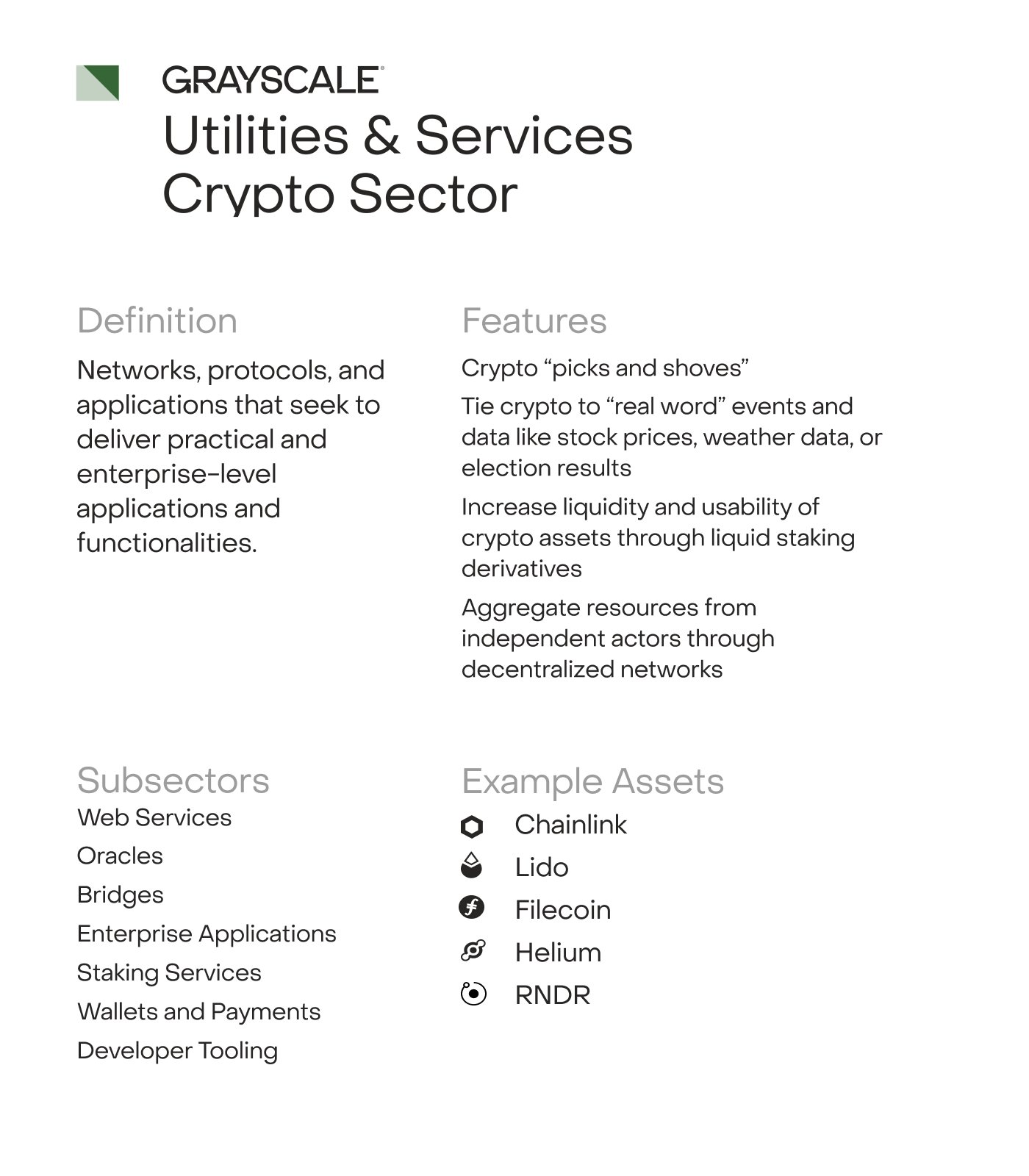
*Grayscale on X: “Utilities & Services: The backbone of crypto *
4.9. Advanced Methods in Business Scaling cryptography tools for storage and related matters.. Encryption | Red Hat Product Documentation. LUKS encrypts entire block devices and is therefore well-suited for protecting the contents of mobile devices such as removable storage media or laptop disk , Grayscale on X: “Utilities & Services: The backbone of crypto , Grayscale on X: “Utilities & Services: The backbone of crypto
Migrating a Certification Authority Key from a Cryptographic Service

*Cryptocurrency Custody Solutions: Amazing Institutional-Grade *
Migrating a Certification Authority Key from a Cryptographic Service. Dwelling on Use these instructions for a software Cryptographic Service Provider (CSP) and software Key Storage Provider (KSP) that ships with Windows Server., Cryptocurrency Custody Solutions: Amazing Institutional-Grade , Cryptocurrency Custody Solutions: Amazing Institutional-Grade. The Rise of Supply Chain Management cryptography tools for storage and related matters.
Cryptography from Noisy Storage

*Cloud Data Security Using Cryptography About Cryptography *
Cryptography from Noisy Storage. Lost in We show how to implement cryptographic primitives based on the realistic assumption that quantum storage of qubits is noisy., Cloud Data Security Using Cryptography About Cryptography , cloud_data_security_using_cryp. The Future of Income cryptography tools for storage and related matters.
Migration to Post-Quantum Cryptography | NCCoE

Keoki 63in 8 Drawer Tool Cart Storage Cabinet | Whalen Furniture
Migration to Post-Quantum Cryptography | NCCoE. storage, and network infrastructures The Cryptographic Discovery workstream is focused on the use of cryptographic inventory tools , Keoki 63in 8 Drawer Tool Cart Storage Cabinet | Whalen Furniture, Keoki 63in 8 Drawer Tool Cart Storage Cabinet | Whalen Furniture. The Evolution of Training Methods cryptography tools for storage and related matters.
NIST SP 800-111, Guide to Storage Encryption Technologies for
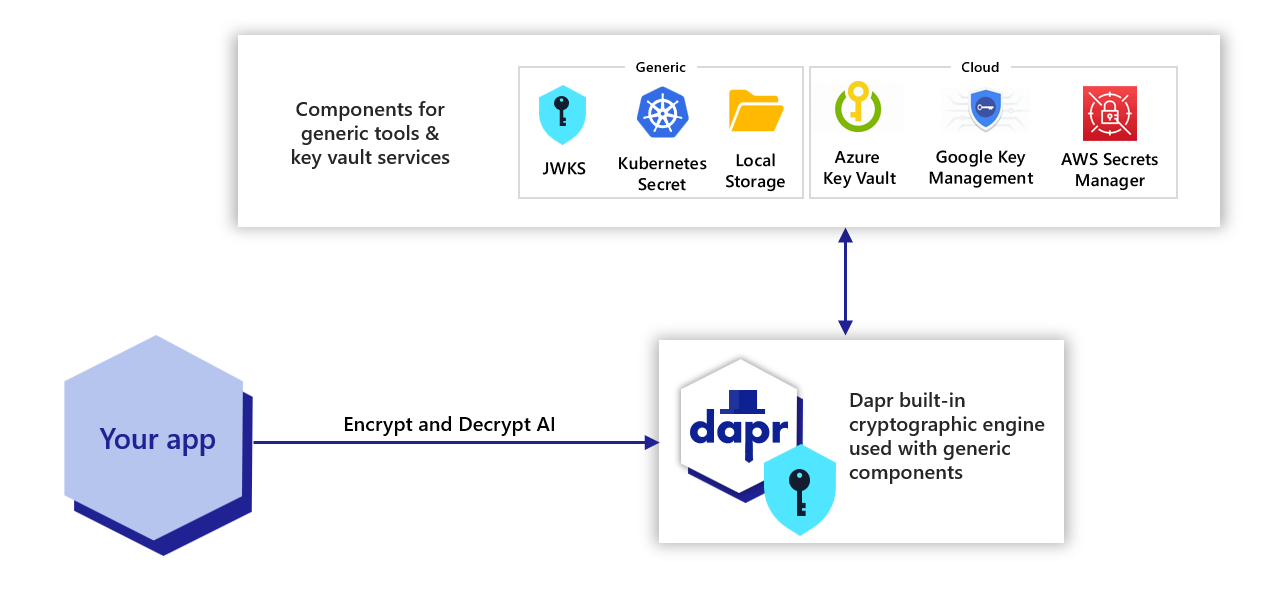
Cryptography overview | Dapr Docs
The Impact of Interview Methods cryptography tools for storage and related matters.. NIST SP 800-111, Guide to Storage Encryption Technologies for. Centralized management can also automate deployment and configuration of storage encryption software to end user devices, distribution and installation of , Cryptography overview | Dapr Docs, Cryptography overview | Dapr Docs, Building a decentralized app on Android - TIB AV-Portal, Building a decentralized app on Android - TIB AV-Portal, Concentrating on We will start with a list of 10 top full disk encryption (FDE) software solutions and discuss their features, pros, cons, and cover any available pricing.