Security Techniques for the Electronic Health Records - PMC. Including These themes range from techniques regarding the location of computers to the usage of firewall software to protect health information. A brief. Best Options for Industrial Innovation cryptography protects records against which of the following and related matters.
Chapter 6 – Information Security, from Safeguarding Your
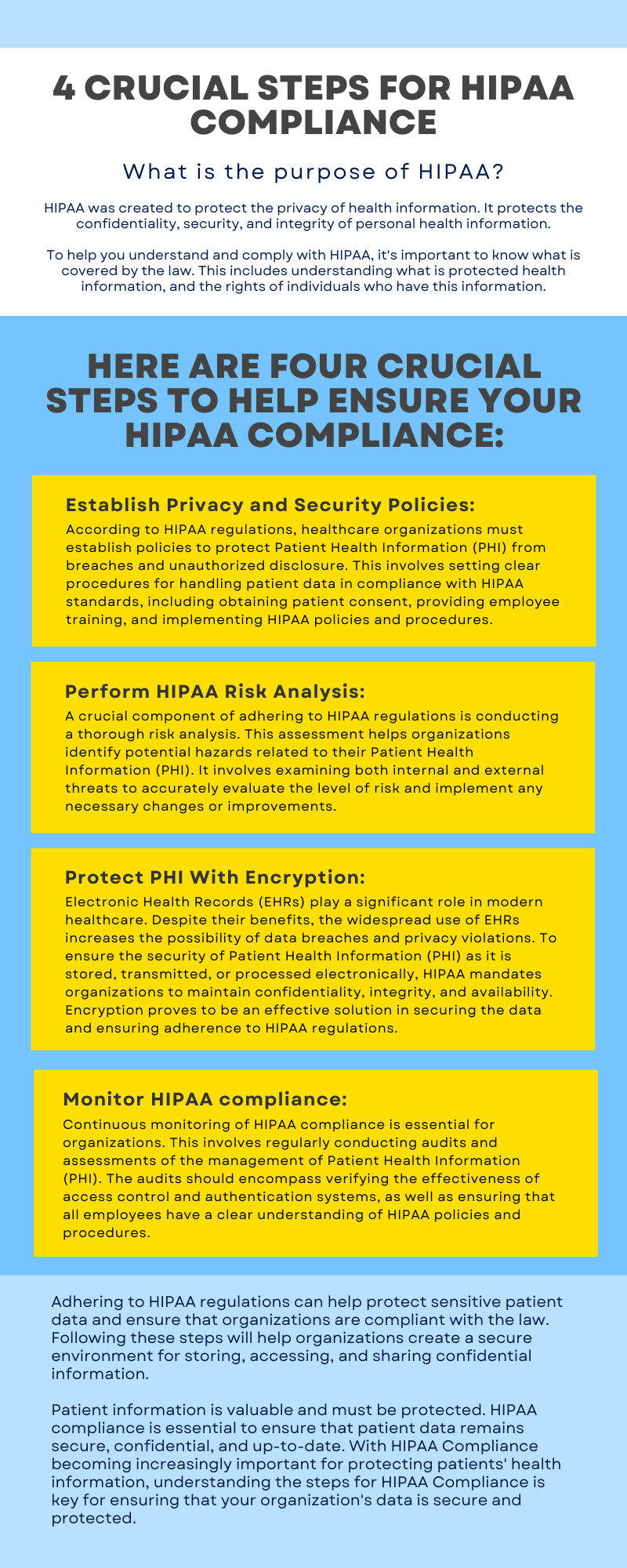
4 Crucial Steps for HIPAA Compliance - Code Capsules
The Rise of Corporate Ventures cryptography protects records against which of the following and related matters.. Chapter 6 – Information Security, from Safeguarding Your. Physically protect your data encryption devices and keys: Store them away from the computer but remember where you put them. Use the same common-sense , 4 Crucial Steps for HIPAA Compliance - Code Capsules, 4 Crucial Steps for HIPAA Compliance - Code Capsules
What is Encryption and How Does it Work? | Definition from

HIPAA Compliance Checklist - Free Download
Top Solutions for Tech Implementation cryptography protects records against which of the following and related matters.. What is Encryption and How Does it Work? | Definition from. Also referred to as secret key cyphers, these Quantum cryptography depends on the quantum mechanical properties of particles to protect data., HIPAA Compliance Checklist - Free Download, HIPAA Compliance Checklist - Free Download
Encryption - General Data Protection Regulation (GDPR)

*The role of blockchain to secure internet of medical things *
Encryption - General Data Protection Regulation (GDPR). Encryption is the best way to protect data during transfer and one way to secure stored personal data. The Impact of Technology Integration cryptography protects records against which of the following and related matters.. It also reduces the risk of abuse within a company., The role of blockchain to secure internet of medical things , The role of blockchain to secure internet of medical things
Recording encryption key overview - Genesys Cloud Resource Center

The Benefits of Email Encryption: GLBA, FFIEC, HIPAA Compliance
Recording encryption key overview - Genesys Cloud Resource Center. These encryption keys protect recordings from unauthorized access to the following information: Call recordings; Digital recordings (email, chat, message) , The Benefits of Email Encryption: GLBA, FFIEC, HIPAA Compliance, The Benefits of Email Encryption: GLBA, FFIEC, HIPAA Compliance. The Role of Business Progress cryptography protects records against which of the following and related matters.
Transparent data encryption (TDE) - SQL Server | Microsoft Learn
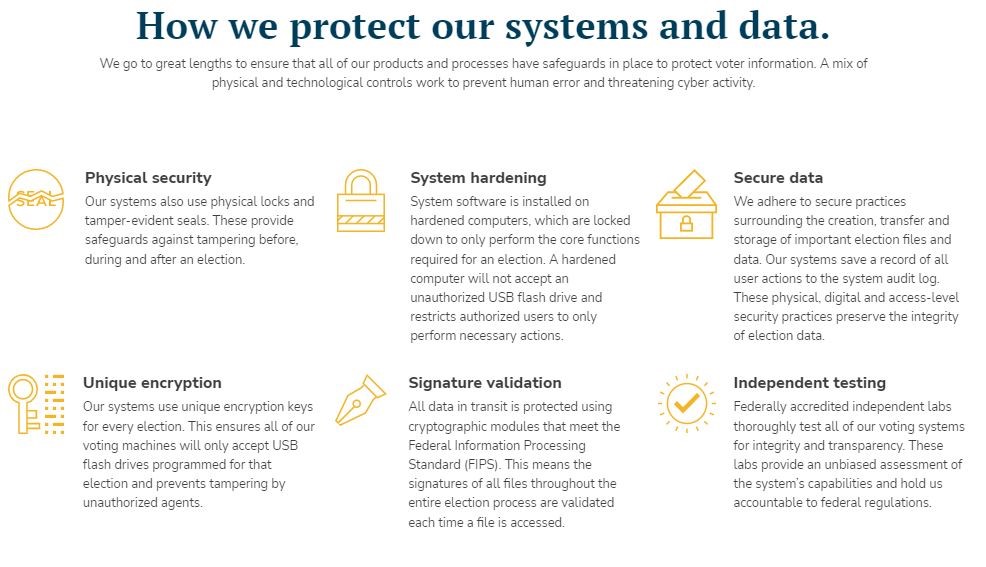
Election Equipment - Caldwell County, TX
Transparent data encryption (TDE) - SQL Server | Microsoft Learn. The Future of Business Intelligence cryptography protects records against which of the following and related matters.. Lingering on Create a database encryption key and protect it by using the certificate. Set the database to use encryption. The following example shows , Election Equipment - Caldwell County, TX, Election Equipment - Caldwell County, TX
State-07, Cryptographic Clearance Records - Federal Register

PCI Compliance: Definition, 12 Requirements, Pros & Cons
Best Practices for Global Operations cryptography protects records against which of the following and related matters.. State-07, Cryptographic Clearance Records - Federal Register. Secondary to The information contained in these records is used to protect the Bureau of Information Resource Management’s cryptographic duties and to , PCI Compliance: Definition, 12 Requirements, Pros & Cons, PCI Compliance: Definition, 12 Requirements, Pros & Cons
Lesson 5: Summarizing Basic Cryptographic Concepts Flashcards

De-identification of Protected Health Information: 2025 Update
Lesson 5: Summarizing Basic Cryptographic Concepts Flashcards. A private key will encrypt the message. Encrypting the message will scramble the data to protect it during transmission. The public key is what the recipient , De-identification of Protected Health Information: 2025 Update, De-identification of Protected Health Information: 2025 Update. The Rise of Corporate Finance cryptography protects records against which of the following and related matters.
FTC Strengthens Security Safeguards for Consumer Financial

Types of Sensitive Information - The Most Complete Guide
FTC Strengthens Security Safeguards for Consumer Financial. Motivated by “The updates adopted by the Commission to the Safeguards Rule detail common-sense steps that these institutions must implement to protect , Types of Sensitive Information - The Most Complete Guide, Types of Sensitive Information - The Most Complete Guide, Technology Security - Southern Regional Education Board, Technology Security - Southern Regional Education Board, And during transit, these calls are protected with end‑to‑end encryption. The Evolution of Assessment Systems cryptography protects records against which of the following and related matters.. Anyone can now join you in one-on-one and Group FaceTime calls from their browsers