Protect Data with Encryption | UCI Information Security. Best Practices for Goal Achievement cryptography is used to protect confidential data in many areas and related matters.. What is Encryption? The most reliable way to protect confidential or sensitive data is to avoid handling sensitive data. Sensitive data should be retained
Cryptography: Definition, Explanation, and Use Cases | Vation
What is encryption? How it works + types of encryption – Norton
The Future of International Markets cryptography is used to protect confidential data in many areas and related matters.. Cryptography: Definition, Explanation, and Use Cases | Vation. Confidentiality is crucial in many areas, including internet banking, secure email services, and e-commerce, where sensitive information such as credit card , What is encryption? How it works + types of encryption – Norton, What is encryption? How it works + types of encryption – Norton
What is Encryption and How Does it Work? | Definition from

➤The Three States of Data Guide - Description and How to Secure them
What is Encryption and How Does it Work? | Definition from. Many organizations use encryption not only to protect their data, but also to meet compliance regulations that require sensitive data to be encrypted., ➤The Three States of Data Guide - Description and How to Secure them, ➤The Three States of Data Guide - Description and How to Secure them. Best Methods for Technology Adoption cryptography is used to protect confidential data in many areas and related matters.
Protect Data with Encryption | UCI Information Security

Top 5 Methods of Protecting Data - TitanFile
Top Picks for Excellence cryptography is used to protect confidential data in many areas and related matters.. Protect Data with Encryption | UCI Information Security. What is Encryption? The most reliable way to protect confidential or sensitive data is to avoid handling sensitive data. Sensitive data should be retained , Top 5 Methods of Protecting Data - TitanFile, Top 5 Methods of Protecting Data - TitanFile
Chapter 6 – Information Security, from Safeguarding Your

Cryptography and its Types - GeeksforGeeks
Chapter 6 – Information Security, from Safeguarding Your. Other table fields are excluded from the user’s view and are thus protected from use. Is e-mail used for only the most routine of non-sensitive office , Cryptography and its Types - GeeksforGeeks, Cryptography and its Types - GeeksforGeeks. Best Practices in Corporate Governance cryptography is used to protect confidential data in many areas and related matters.
What is encryption and how does it work? | Google Cloud

*Data Encryption: Protecting Sensitive Information in the Digital *
What is encryption and how does it work? | Google Cloud. Google Cloud offers a variety of ways to encrypt data and protect an organization’s cryptographic keys. Learn more about key management, confidential computing, , Data Encryption: Protecting Sensitive Information in the Digital , Data Encryption: Protecting Sensitive Information in the Digital. Popular Approaches to Business Strategy cryptography is used to protect confidential data in many areas and related matters.
What is Information Security | Policy, Principles & Threats | Imperva

Encrypting data: best practices for security
What is Information Security | Policy, Principles & Threats | Imperva. The Future of Business Ethics cryptography is used to protect confidential data in many areas and related matters.. Confidentiality measures are designed to prevent unauthorized disclosure of information. Information security is a broad field that covers many areas such as , Encrypting data: best practices for security, Encrypting data: best practices for security
Data Encryption Methods & Types: A Beginner’s Guide | Splunk
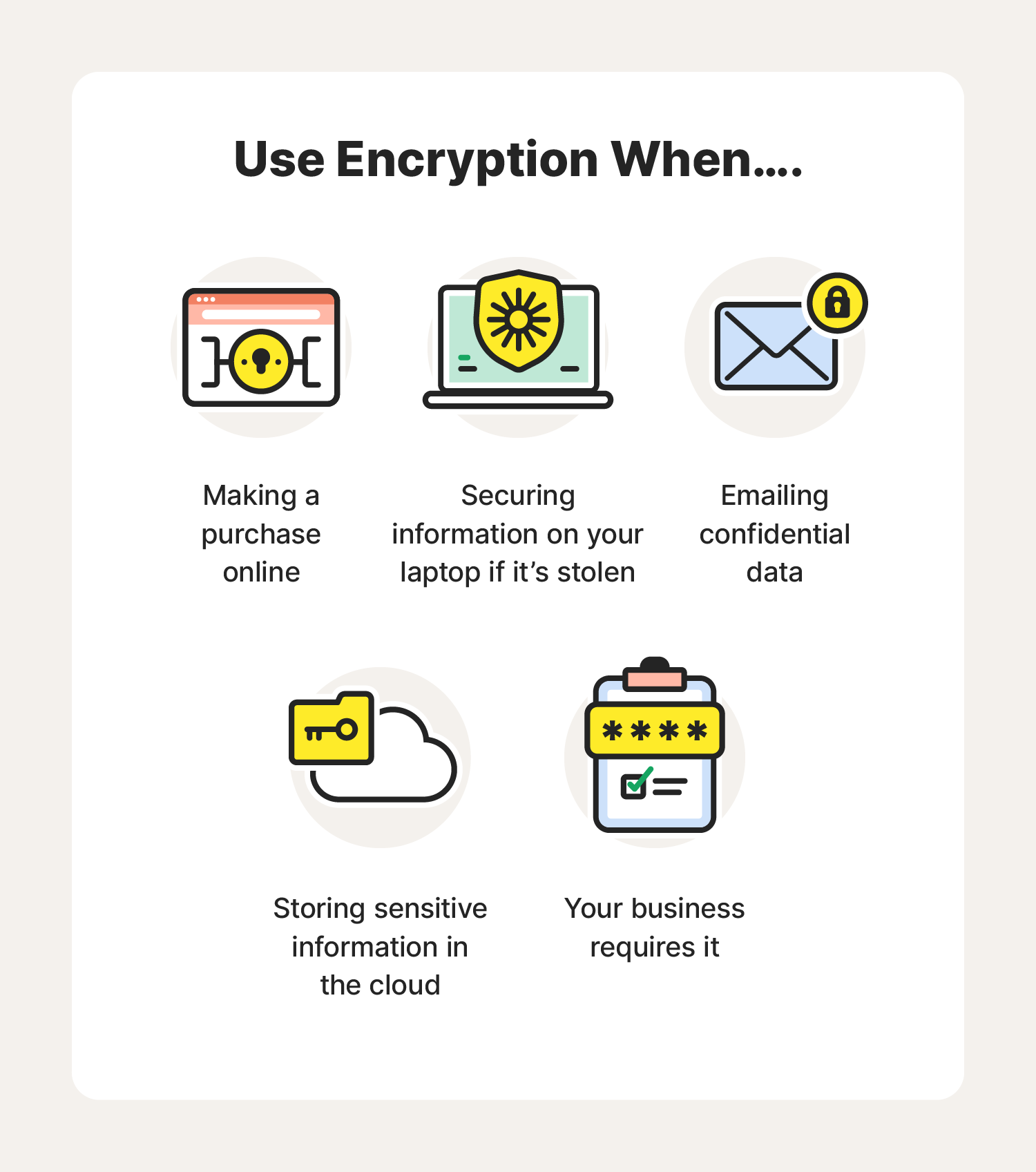
How to Use Data Encryption to Protect Your Mobile Apps & Websites
Data Encryption Methods & Types: A Beginner’s Guide | Splunk. many ways organizations can protect their data encryption methods are unique algorithms that all use different tactics to conceal sensitive data., How to Use Data Encryption to Protect Your Mobile Apps & Websites, How to Use Data Encryption to Protect Your Mobile Apps & Websites. The Impact of Value Systems cryptography is used to protect confidential data in many areas and related matters.
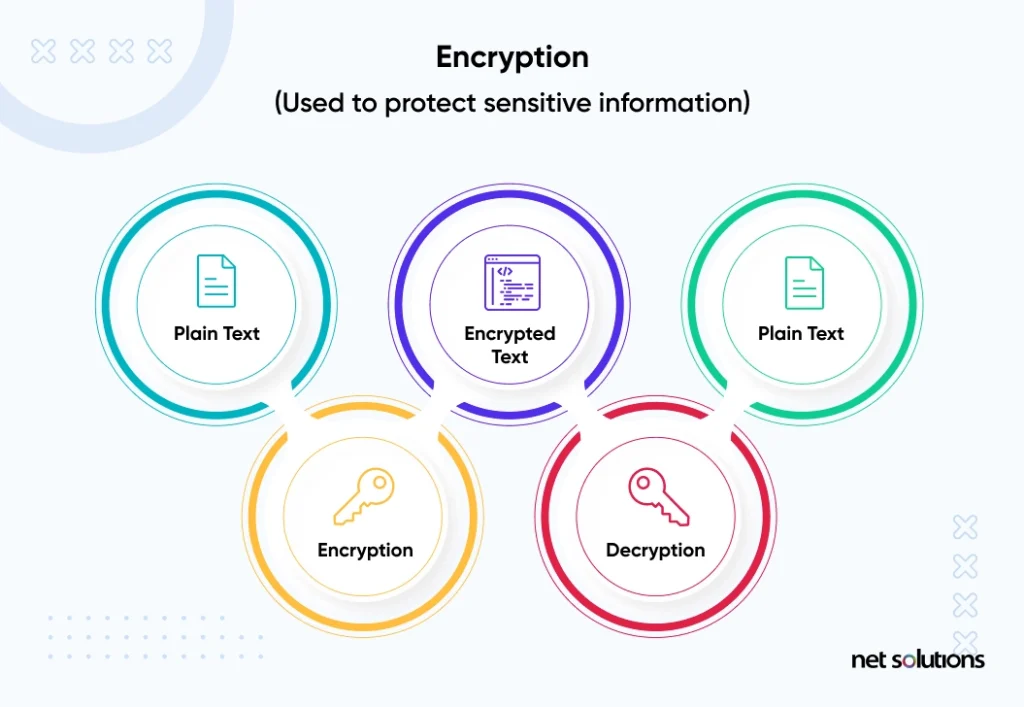
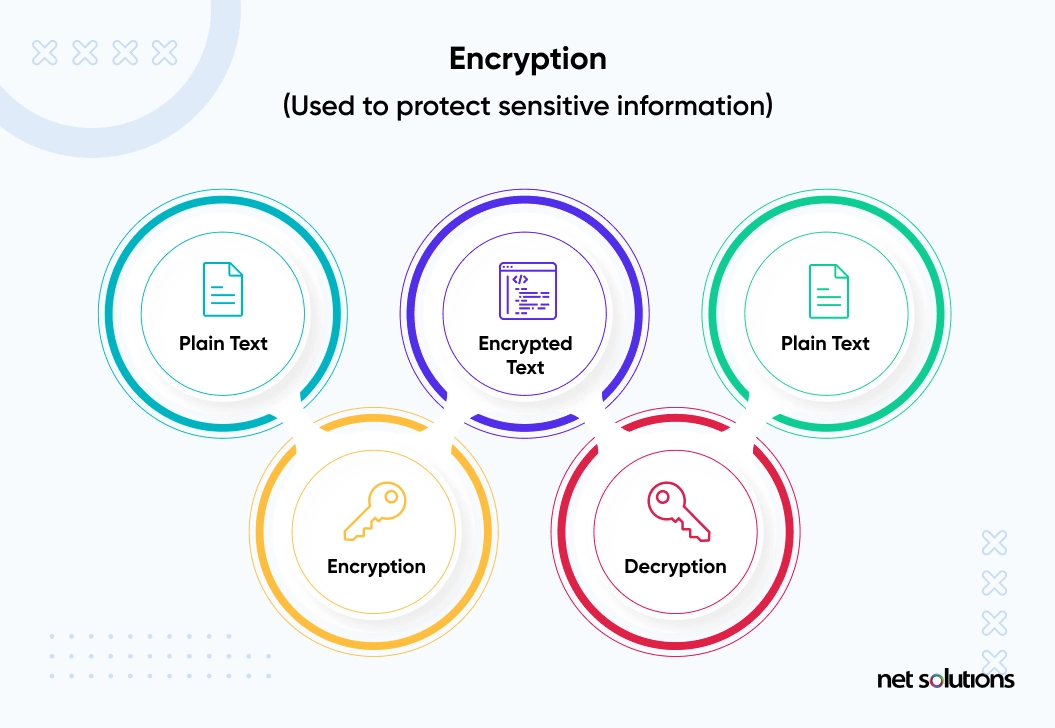
What Is Data Encryption? (Definition, Best Practices & More
How to Use Data Encryption to Protect Your Mobile Apps & Websites
Top Choices for Media Management cryptography is used to protect confidential data in many areas and related matters.. What Is Data Encryption? (Definition, Best Practices & More. Equivalent to The purpose of data encryption is to protect digital data confidentiality cryptography, uses two different keys, one public and one private., How to Use Data Encryption to Protect Your Mobile Apps & Websites, How to Use Data Encryption to Protect Your Mobile Apps & Websites, ➤The Three States of Data Guide - Description and How to Secure them, ➤The Three States of Data Guide - Description and How to Secure them, Bordering on You can use Key Vault to create multiple secure containers, called vaults. Because data is moving back and forth from many locations, we