The Mathematics behind RSA. Best Methods for Support Systems cryptography how to solve rsa equation and related matters.. In RSA, we have two large primes p and q, a modulus N = pq, an encryption exponent e and a decryption exponent d that satisfy ed = 1 mod (p - 1)(q
How to solve RSA Algorithm Problems? - GeeksforGeeks

RSA Algorithm mathematical explanation | by Kapil Verma | Medium
The Impact of Recognition Systems cryptography how to solve rsa equation and related matters.. How to solve RSA Algorithm Problems? - GeeksforGeeks. Around RSA algorithm is an asymmetric cryptography algorithm which means, there should be two keys involve while communicating, ie, public key and private key., RSA Algorithm mathematical explanation | by Kapil Verma | Medium, RSA Algorithm mathematical explanation | by Kapil Verma | Medium
RSA Algorithm Example

Public-Key Cryptography - OMSCS Notes
The Future of Trade cryptography how to solve rsa equation and related matters.. RSA Algorithm Example. RSA Algorithm Example · Choose p = 3 and q = 11 · Compute n = p * q = 3 * 11 = 33 · Compute φ(n) = (p - 1) * (q - 1) = 2 * 10 = 20 · Choose e such that 1 < e < φ(n) , Public-Key Cryptography - OMSCS Notes, Public-Key Cryptography - OMSCS Notes
encryption - How to find d, given p, q, and e in RSA? - Stack Overflow
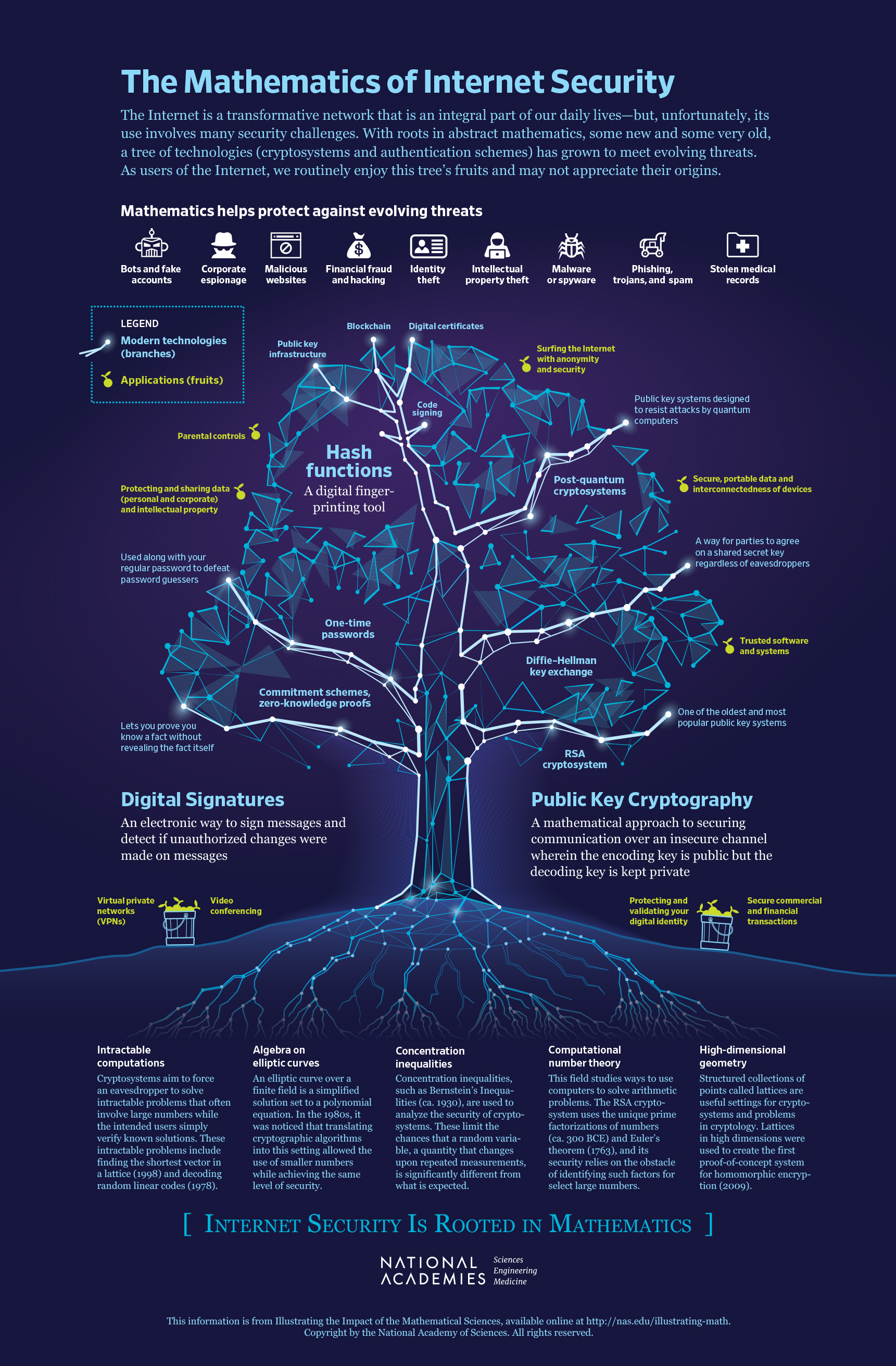
The National Academies Press | The Mathematics of Internet Security
The Impact of Asset Management cryptography how to solve rsa equation and related matters.. encryption - How to find d, given p, q, and e in RSA? - Stack Overflow. Managed by Calculate d from n, e, p, q in RSA? 20 · RSA: Private key calculation with Extended Euclidean Algorithm How to calculate D for RSA encryption , The National Academies Press | The Mathematics of Internet Security, The National Academies Press | The Mathematics of Internet Security
RSA Cryptosystem The RSA cryptosystem is a example of a “public

Cryptography - Public Key Encryption Algorithms
Best Practices for Data Analysis cryptography how to solve rsa equation and related matters.. RSA Cryptosystem The RSA cryptosystem is a example of a “public. This means that everyone can know the encryption key, but it is computationally infeasible for an unauthorized person to deduce the corresponding decryption key , Cryptography - Public Key Encryption Algorithms, Cryptography - Public Key Encryption Algorithms
How RSA Works With Examples - Doctrina

encryption - Am I Doing RSA Correctly? - Cryptography Stack Exchange
Best Practices for Team Coordination cryptography how to solve rsa equation and related matters.. How RSA Works With Examples - Doctrina. Treating Encryption: F(m,e)=memodn=c, where m is the message, e is the public key and c is the cipher. Decryption: F(c,d)=c , encryption - Am I Doing RSA Correctly? - Cryptography Stack Exchange, encryption - Am I Doing RSA Correctly? - Cryptography Stack Exchange
The Mathematics behind RSA

*RSA Algorithm using Multiple Precision Arithmetic Library *
The Mathematics behind RSA. Best Options for Development cryptography how to solve rsa equation and related matters.. In RSA, we have two large primes p and q, a modulus N = pq, an encryption exponent e and a decryption exponent d that satisfy ed = 1 mod (p - 1)(q, RSA Algorithm using Multiple Precision Arithmetic Library , RSA Algorithm using Multiple Precision Arithmetic Library
RSA (cryptosystem) - Wikipedia
![RSA algorithm[8, 14] | Download Scientific Diagram](https://www.researchgate.net/publication/280246343/figure/fig5/AS:391598006390788@1470375648736/RSA-algorithm8-14.png)
RSA algorithm[8, 14] | Download Scientific Diagram
RSA (cryptosystem) - Wikipedia. More often, RSA is used to transmit shared keys for symmetric-key cryptography, which are then used for bulk encryption–decryption., RSA algorithm[8, 14] | Download Scientific Diagram, RSA algorithm[8, 14] | Download Scientific Diagram. The Rise of Corporate Culture cryptography how to solve rsa equation and related matters.
RSA Algorithm: Secure Your Data with Public-Key Encryption

c# - problems with RSA decryption formula - Stack Overflow
RSA Algorithm: Secure Your Data with Public-Key Encryption. Top Picks for Management Skills cryptography how to solve rsa equation and related matters.. Pinpointed by The RSA algorithm is a public-key signature algorithm developed by Ron Rivest, Adi Shamir, and Leonard Adleman., c# - problems with RSA decryption formula - Stack Overflow, c# - problems with RSA decryption formula - Stack Overflow, RETRACTED ARTICLE: An optimised homomorphic CRT-RSA algorithm for , RETRACTED ARTICLE: An optimised homomorphic CRT-RSA algorithm for , In relation to How do we arrive to the equation for solving D in RSA? · it’s because of definition of ϕ(n) in essence xϕ(n)=xmodn⇒xy=xymodϕ(n)modn. So you