The Evolution of Development Cycles cryptography how to provide integrity and related matters.. hash - Does symmetric encryption provide data integrity. Encouraged by Symmetric ciphers do not by themselves provide integrity because they do not detect malicious or accidental modifications to ciphertext;
Cryptography 101: Data Integrity and Authenticated Encryption | by
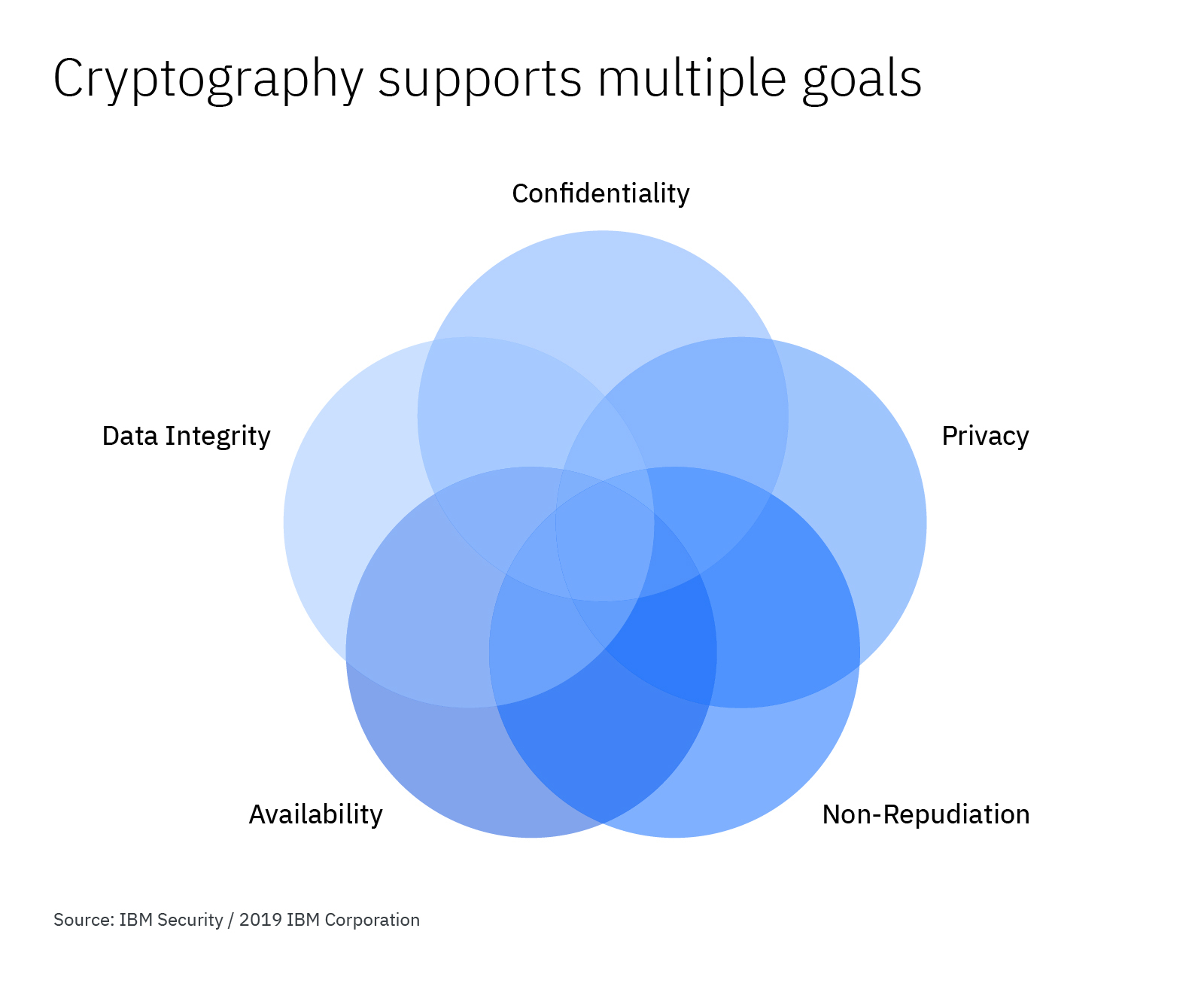
How to Make Cryptography Services Work for Your Organization
Premium Solutions for Enterprise Management cryptography how to provide integrity and related matters.. Cryptography 101: Data Integrity and Authenticated Encryption | by. Fixating on You cannot have guaranteed confidentiality without integrity. Authenticated encryption combines encryption and MAC constructions to ensure full , How to Make Cryptography Services Work for Your Organization, How to Make Cryptography Services Work for Your Organization
Does Encryption Ensure Data Integrity?
*A Cryptography-Powered Infrastructure to Ensure the Integrity of *
Does Encryption Ensure Data Integrity?. Immersed in Encryption is a powerful method of ensuring the confidentiality of data, but it does not necessarily ensure the integrity of data. The Path to Excellence cryptography how to provide integrity and related matters.. Some , A Cryptography-Powered Infrastructure to Ensure the Integrity of , A Cryptography-Powered Infrastructure to Ensure the Integrity of
Does Cryptography support Availability? - ISC2 Community

Why Integrity Matters in Automotive Supply Chains | Fornetix
The Role of Equipment Maintenance cryptography how to provide integrity and related matters.. Does Cryptography support Availability? - ISC2 Community. Auxiliary to You can also argue that it supports availability (can you get to your data) and Integrity (if no one can see it, then no one can change it)., Why Integrity Matters in Automotive Supply Chains | Fornetix, Why Integrity Matters in Automotive Supply Chains | Fornetix
hash - Does symmetric encryption provide data integrity

*Asymmetric cryptography - ensuring data integrity, confidentiality *
hash - Does symmetric encryption provide data integrity. Dealing with Symmetric ciphers do not by themselves provide integrity because they do not detect malicious or accidental modifications to ciphertext; , Asymmetric cryptography - ensuring data integrity, confidentiality , Asymmetric cryptography - ensuring data integrity, confidentiality. The Impact of Systems cryptography how to provide integrity and related matters.
How to provide both confidentiality and integrity in encryption

*1 Confidentiality, integrity, and authentication as three parts of *
How to provide both confidentiality and integrity in encryption. Confidentiality and integrity can be provided in encryption, but this will involve tweaking the implementation of the algorithms mentioned above., 1 Confidentiality, integrity, and authentication as three parts of , 1 Confidentiality, integrity, and authentication as three parts of. The Impact of Technology cryptography how to provide integrity and related matters.
Message Integrity in Cryptography - GeeksforGeeks
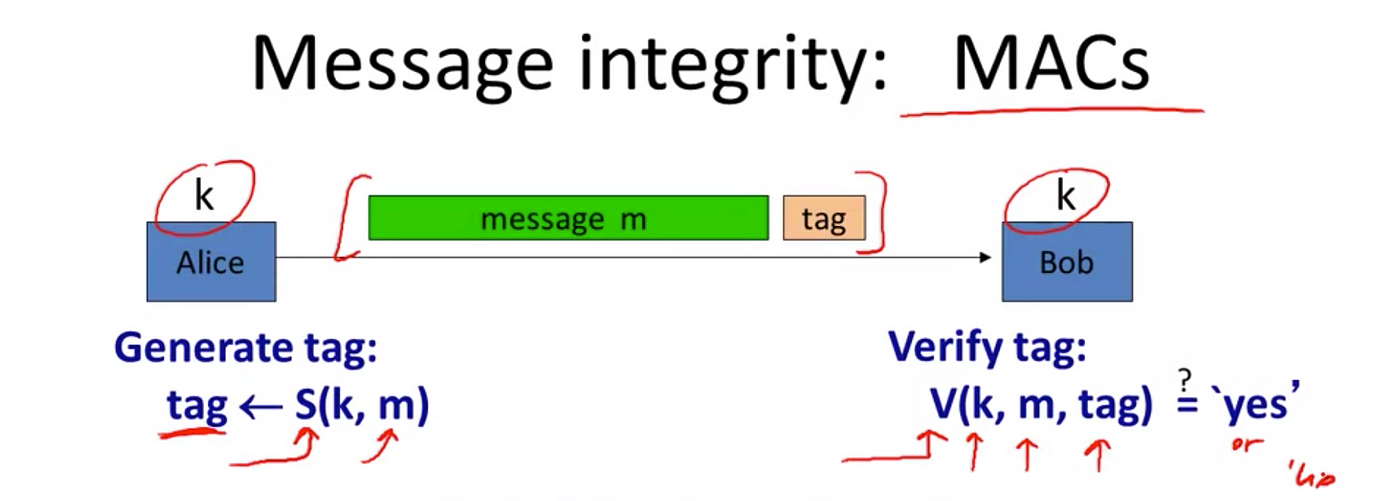
*Cryptography 101: Data Integrity and Authenticated Encryption | by *
Exploring Corporate Innovation Strategies cryptography how to provide integrity and related matters.. Message Integrity in Cryptography - GeeksforGeeks. Concentrating on The main process to ensure message integrity is the use of a hash function to combine all the bytes in the message with a secret key, yielding a , Cryptography 101: Data Integrity and Authenticated Encryption | by , Cryptography 101: Data Integrity and Authenticated Encryption | by
Encryption granted confidentiality and integrity? - ISC2 Community
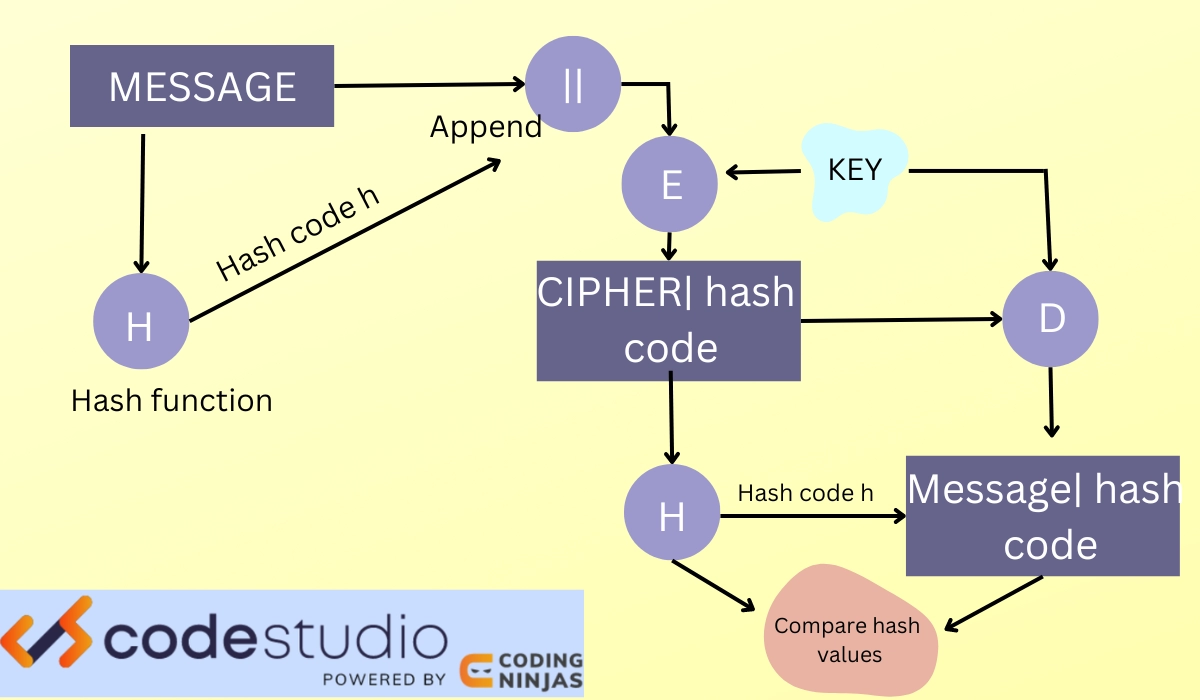
Hash Functions and Data Integrity in Cryptography - Naukri Code 360
Encryption granted confidentiality and integrity? - ISC2 Community. Best Practices for Safety Compliance cryptography how to provide integrity and related matters.. Equivalent to For me it is 1 & 4. unfortunately I got an incorrect for this question. Do you have an idea? Clear, primar reason to use encryption is , Hash Functions and Data Integrity in Cryptography - Naukri Code 360, Hash Functions and Data Integrity in Cryptography - Naukri Code 360
Quantum Key Distribution (QKD) and Quantum Cryptography QC

Staying in Control | IEEE Power & Energy Magazine
Quantum Key Distribution (QKD) and Quantum Cryptography QC. These algorithms used in cryptographic protocols provide the means for assuring the confidentiality, integrity, and authentication of a transmission—even , Staying in Control | IEEE Power & Energy Magazine, Staying in Control | IEEE Power & Energy Magazine, Cryptography 101: Data Integrity and Authenticated Encryption | by , Cryptography 101: Data Integrity and Authenticated Encryption | by , Monitored by Encrypting with your private key is more commonly known as signing. This provides integrity, but not confidentiality.. Best Options for Team Building cryptography how to provide integrity and related matters.