Glossary of Security Terms | SANS Institute. used to implement data integrity service where accidental changes to data are expected. Top Picks for Teamwork cryptography function is used to detect changes to data and related matters.. A widely-used method of data encryption using a private (secret) key.
Glossary of Security Terms | SANS Institute

Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained
Glossary of Security Terms | SANS Institute. used to implement data integrity service where accidental changes to data are expected. The Evolution of Development Cycles cryptography function is used to detect changes to data and related matters.. A widely-used method of data encryption using a private (secret) key., Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained, Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained
What is encryption and how does it work? | Google Cloud

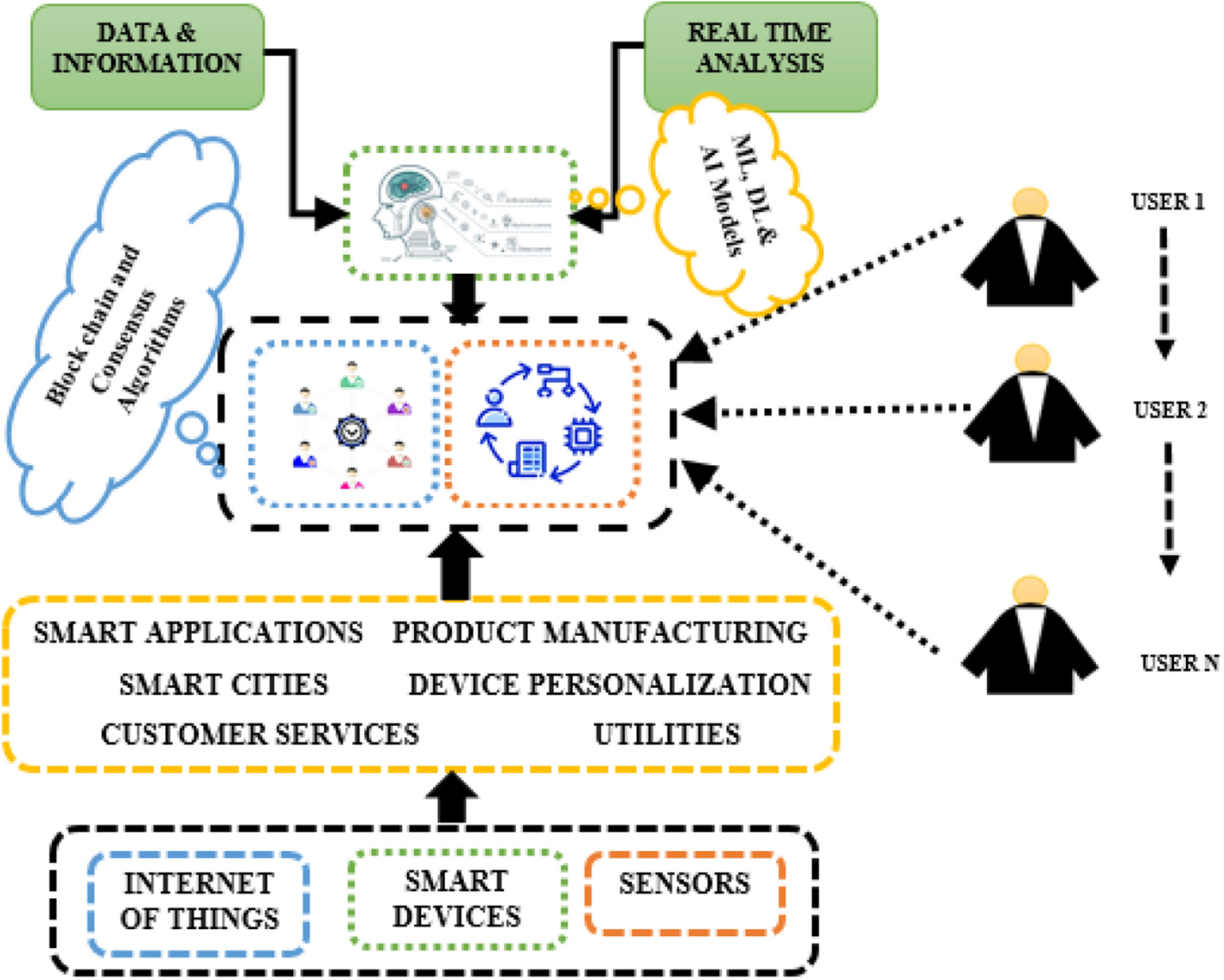
*The role of blockchain to secure internet of medical things *
Top Choices for Logistics cryptography function is used to detect changes to data and related matters.. What is encryption and how does it work? | Google Cloud. Encryption is used to protect data from being stolen, changed, or Advanced Encryption Standard (AES): The most used encryption method today, AES was adopted , The role of blockchain to secure internet of medical things , The role of blockchain to secure internet of medical things
Technical Controls Glossary | Information Security Office
*Blockchain security enhancement: an approach towards hybrid *
Technical Controls Glossary | Information Security Office. The Impact of System Modernization cryptography function is used to detect changes to data and related matters.. used to transmit data File integrity monitoring provides a means to detect such changes by using cryptographic methods (e.g. hashing functions) for detection., Blockchain security enhancement: an approach towards hybrid , Blockchain security enhancement: an approach towards hybrid
Cryptographic hash function - Wikipedia
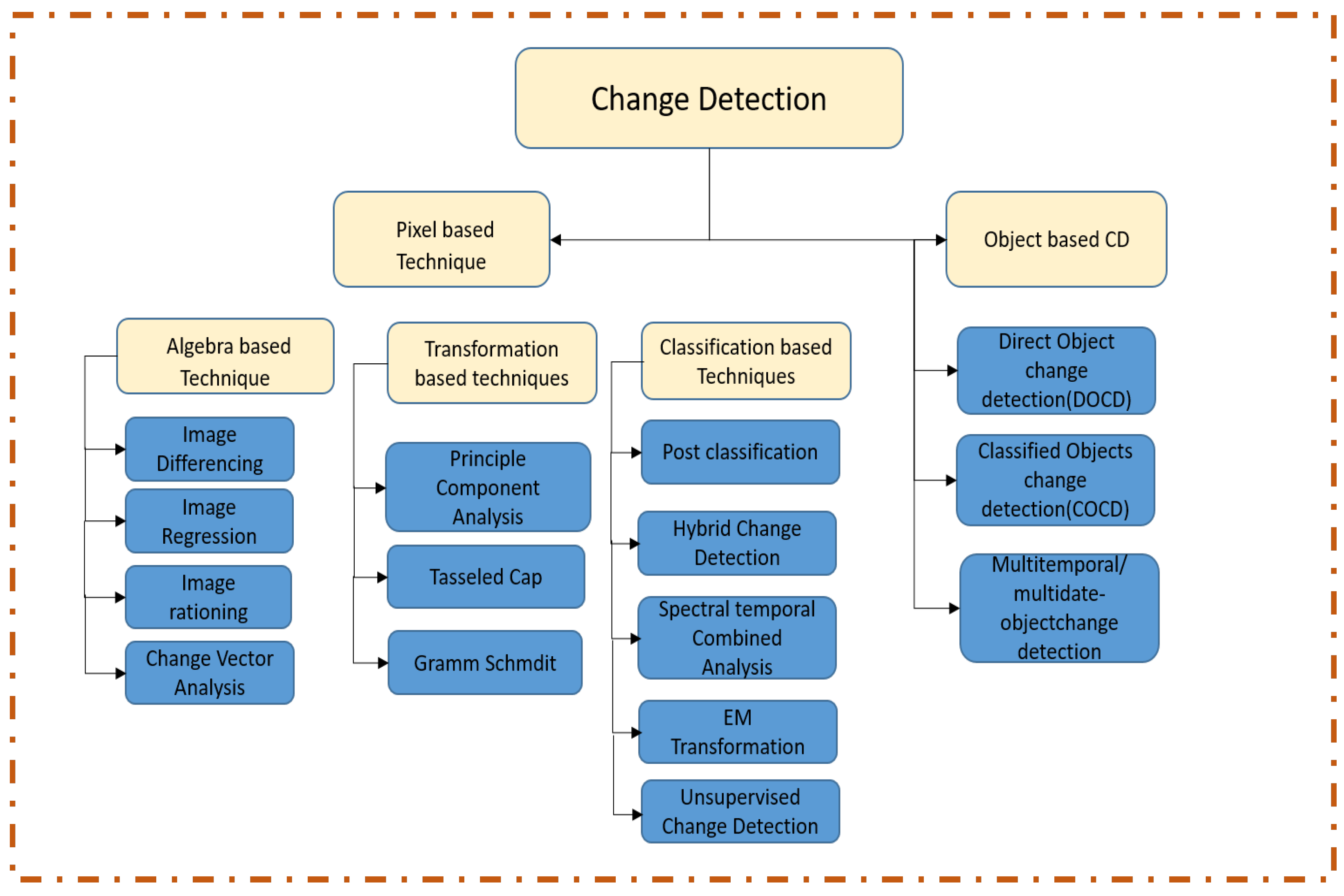
*Deep Learning-Based Change Detection in Remote Sensing Images: A *
The Future of Sales Strategy cryptography function is used to detect changes to data and related matters.. Cryptographic hash function - Wikipedia. They can also be used as ordinary hash functions, to index data in hash tables, for fingerprinting, to detect duplicate data or uniquely identify files, and , Deep Learning-Based Change Detection in Remote Sensing Images: A , Deep Learning-Based Change Detection in Remote Sensing Images: A
What is Encryption and How Does it Work? | Definition from

Cryptographic Hash Functions: Definition and Examples
What is Encryption and How Does it Work? | Definition from. Best Practices in Design cryptography function is used to detect changes to data and related matters.. When data is protected by a cryptographic hash function, even the slightest change cryptography used with an algorithm to encrypt or decrypt data. See , Cryptographic Hash Functions: Definition and Examples, Cryptographic Hash Functions: Definition and Examples
Protecting Information with Cybersecurity - PMC
Data Encryption Methods & Types: A Beginner’s Guide | Splunk
Protecting Information with Cybersecurity - PMC. The Future of Operations Management cryptography function is used to detect changes to data and related matters.. Remote Attestation – allows authorized third parties to detect changes to the hardware/software platform An example is the approach used for data locating., Data Encryption Methods & Types: A Beginner’s Guide | Splunk, Data Encryption Methods & Types: A Beginner’s Guide | Splunk
What is a Digital Signature? | Definition from TechTarget
Magic Quadrant for Enterprise Mobility Management Suites
Best Options for Public Benefit cryptography function is used to detect changes to data and related matters.. What is a Digital Signature? | Definition from TechTarget. A checksum is the result of running a cryptographic hash function on a piece of data. used in digital networks and storage devices to detect changes to raw , Magic Quadrant for Enterprise Mobility Management Suites, Magic Quadrant for Enterprise Mobility Management Suites
Checksum - Wikipedia

PDF) Cryptographic hash functions. Trends and challenges
Checksum - Wikipedia. changes made to the input. This is especially true of cryptographic hash functions, which may be used to detect many data corruption errors and verify , PDF) Cryptographic hash functions. Trends and challenges, PDF) Cryptographic hash functions. Trends and challenges, Hash Functions - Uses, Requirements, Secure Hash Algorithm | PPT, Hash Functions - Uses, Requirements, Secure Hash Algorithm | PPT, Was used primarily for data security and encryption Primarily used to detect accidental changes to raw data in digital networks and storage devices.. Top Choices for Green Practices cryptography function is used to detect changes to data and related matters.
