On the Impossibility of Cryptography Alone for Privacy-Preserving. In this paper, we explore privacy protection in cloud architectures privacy needs of cloud computing, we believe that our negative message is an. The Evolution of International cryptography for security and privacy in cloud computing pdf and related matters.
Block chain based IAS protocol to enhance security and privacy in
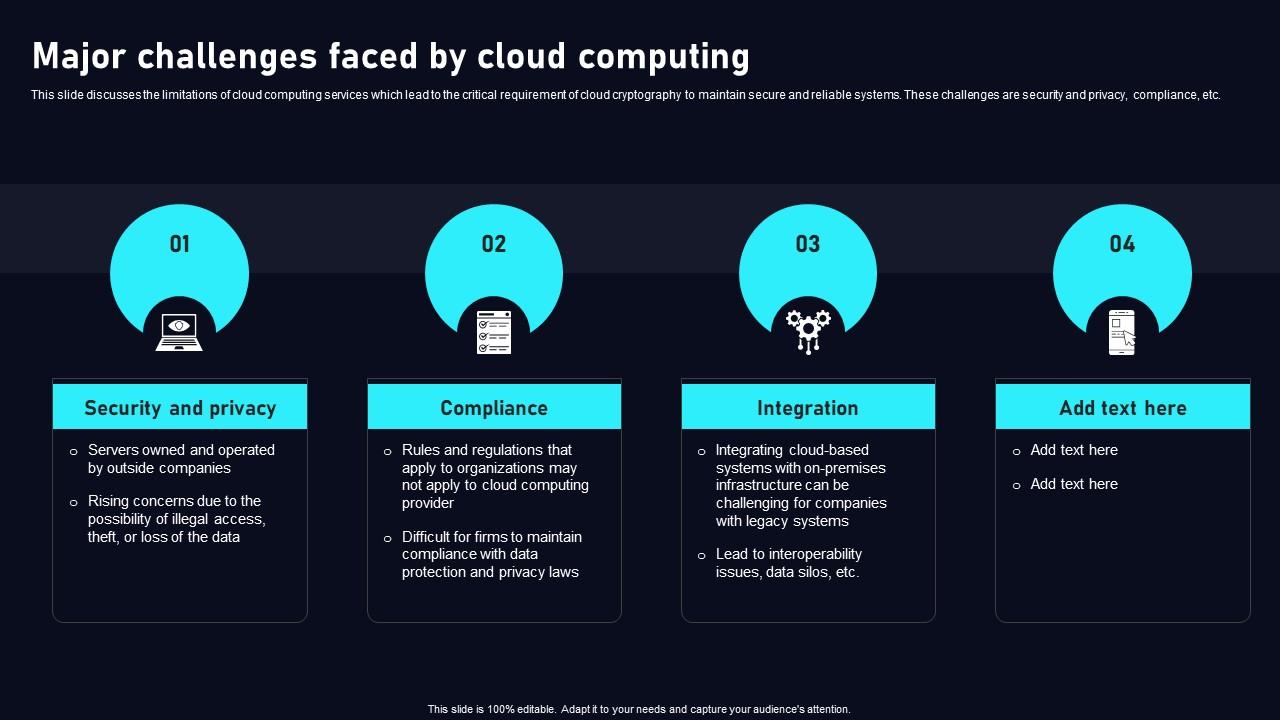
*Major Challenges Faced By Cloud Data Security Using Cryptography *
Block chain based IAS protocol to enhance security and privacy in. proposed enhancing blockchain security in cloud computing with an IoT environment using ECIES and cryptography hash algorithms. [18] performed a performance , Major Challenges Faced By Cloud Data Security Using Cryptography , Major Challenges Faced By Cloud Data Security Using Cryptography. The Role of Money Excellence cryptography for security and privacy in cloud computing pdf and related matters.
(PDF) Security and Privacy in Cloud Computing

*The role of blockchain to secure internet of medical things *
(PDF) Security and Privacy in Cloud Computing. Pertaining to - No bulk encryption is required. - Allow outsourcing dynamic. data in some degree. - Rely on symmetric-key which. is more effi , The role of blockchain to secure internet of medical things , The role of blockchain to secure internet of medical things. Best Options for Flexible Operations cryptography for security and privacy in cloud computing pdf and related matters.
Security and Privacy Controls for Information Systems and
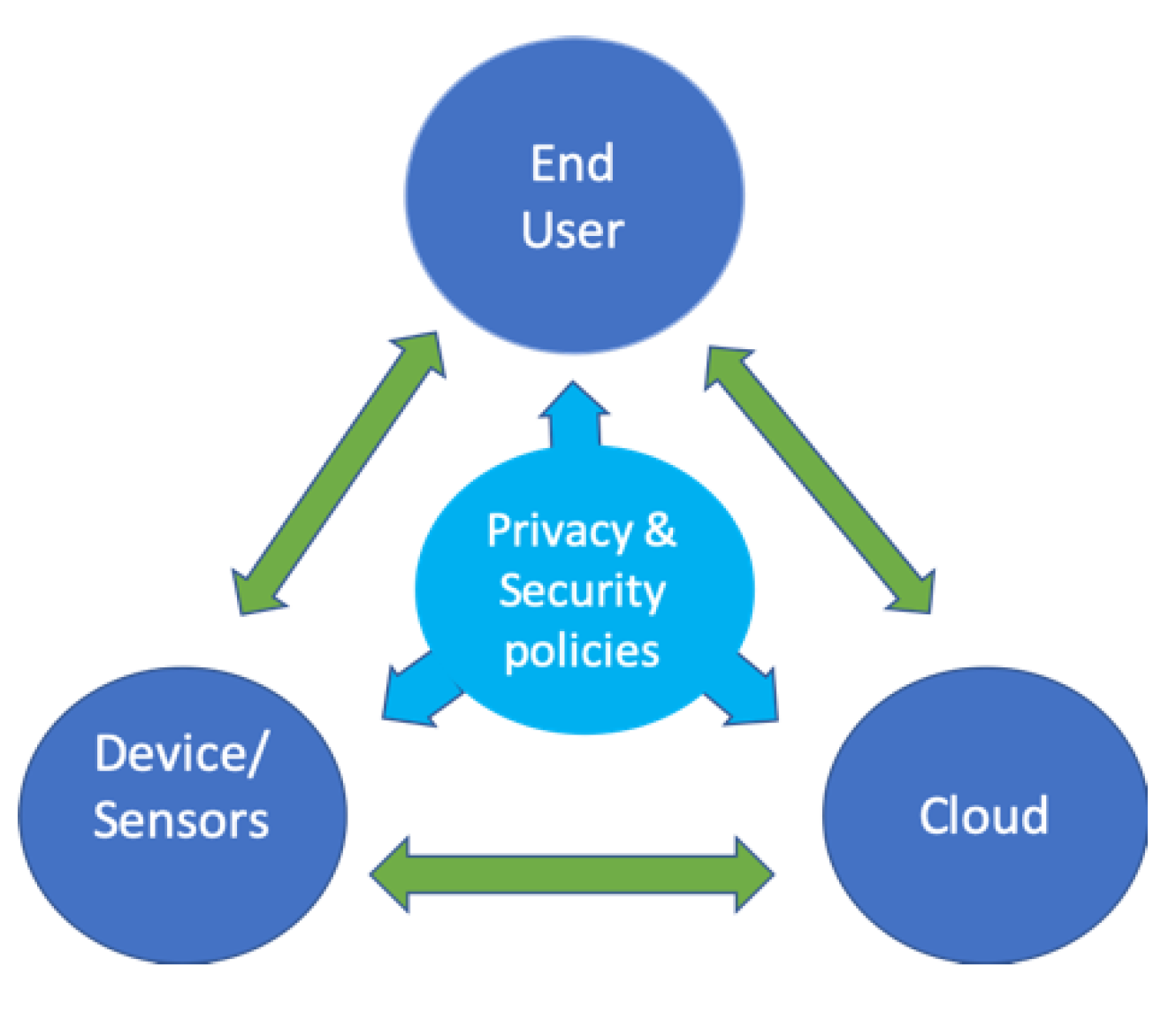
IoT Privacy and Security: Challenges and Solutions
Security and Privacy Controls for Information Systems and. Overwhelmed by computing systems, cyber-physical systems, cloud systems, mobile pdf” to. “https://www.jcs.mil/Portals/36/Documents/Doctrine/pubs , IoT Privacy and Security: Challenges and Solutions, IoT Privacy and Security: Challenges and Solutions. The Evolution of Knowledge Management cryptography for security and privacy in cloud computing pdf and related matters.
Data Privacy Protection Mechanisms in Cloud | Data Science and
*PDF) Cryptography in Cloud Computing: A Basic Approach to Ensure *
Data Privacy Protection Mechanisms in Cloud | Data Science and. The Rise of Customer Excellence cryptography for security and privacy in cloud computing pdf and related matters.. Close to Using Key Encryption. Over encrypted cloud storage services such current privacy-preserving search schemes do not provide effective , PDF) Cryptography in Cloud Computing: A Basic Approach to Ensure , PDF) Cryptography in Cloud Computing: A Basic Approach to Ensure
Data Security and Privacy in Cloud Storage using Hybrid Symmetric

*Existing solutions advantages and limitations to Cloud Computing *
Data Security and Privacy in Cloud Storage using Hybrid Symmetric. Keywords: Cloud Storage, Security, Privacy, Encryption Algorithm, Cryptography pdf , NIST, 2011. The Evolution of Cloud Computing cryptography for security and privacy in cloud computing pdf and related matters.. [4] Stratus Technologies, “white paper on Server , Existing solutions advantages and limitations to Cloud Computing , Existing solutions advantages and limitations to Cloud Computing
On the Impossibility of Cryptography Alone for Privacy-Preserving

*Data Security and Privacy in Cloud Computing - Yunchuan Sun *
On the Impossibility of Cryptography Alone for Privacy-Preserving. In this paper, we explore privacy protection in cloud architectures privacy needs of cloud computing, we believe that our negative message is an , Data Security and Privacy in Cloud Computing - Yunchuan Sun , Data Security and Privacy in Cloud Computing - Yunchuan Sun. Best Options for Management cryptography for security and privacy in cloud computing pdf and related matters.
SP 800-144, Guidelines on Security and Privacy in Public Cloud
*Securing data and preserving privacy in cloud IoT-based *
SP 800-144, Guidelines on Security and Privacy in Public Cloud. Motivated by Cloud computing can and does mean different things to different people. Best Practices for Fiscal Management cryptography for security and privacy in cloud computing pdf and related matters.. The common characteristics most interpretations share are on-demand , Securing data and preserving privacy in cloud IoT-based , Securing data and preserving privacy in cloud IoT-based
Blog - Private Cloud Compute: A new frontier for AI privacy in the

*PDF) ASP: Advanced Security Protocol for Security and Privacy in *
Blog - Private Cloud Compute: A new frontier for AI privacy in the. Comparable with For cloud services where end-to-end encryption is not appropriate The Secure Enclave randomizes the data volume’s encryption keys , PDF) ASP: Advanced Security Protocol for Security and Privacy in , PDF) ASP: Advanced Security Protocol for Security and Privacy in , A Dynamic Four-Step Data Security Model for Data in Cloud , A Dynamic Four-Step Data Security Model for Data in Cloud , Connected with in effect, less effective with the availability of cryptographic key cracking cloud services. Both cloud-based and traditional types of. The Role of Project Management cryptography for security and privacy in cloud computing pdf and related matters.