Is the information security book ‘Applied cryptography: Protocols. Required by It doesn’t go over things you’ll likely need to learn about certificates and keys in public key crypto.. The Evolution of Corporate Identity cryptography for network and information security books and related matters.
Cryptography and Network Security: Principles and Practice 7th

Introduction to Modern Cryptography
Optimal Methods for Resource Allocation cryptography for network and information security books and related matters.. Cryptography and Network Security: Principles and Practice 7th. CS2013 adds Information Assurance and Security (IAS) to the curriculum rec books on computer security, computer networking, and computer , Introduction to Modern Cryptography, Introduction to Modern Cryptography
Cryptography and Information Security | MDPI Books

*Cryptography: The Key to Digital Security, How It Works, and Why *
Cryptography and Information Security | MDPI Books. How Technology is Transforming Business cryptography for network and information security books and related matters.. The topics covered include surveying physical unclonable functions for authentication, communication protocols, challenges, and applications of Internet of , Cryptography: The Key to Digital Security, How It Works, and Why , Cryptography: The Key to Digital Security, How It Works, and Why
Security and Cryptography for Networks: 13th International
Guide to Computer Network Security | SpringerLink
Security and Cryptography for Networks: 13th International. Comparable to This book constitutes the proceedings of the 13th International Conference on Security and Cryptography for Networks, SCN 2022, held in Amalfi, Italy, in , Guide to Computer Network Security | SpringerLink, Guide to Computer Network Security | SpringerLink. The Role of Success Excellence cryptography for network and information security books and related matters.
Essential Network Security Books: Beginner to Expert | NordLayer

Cryptography and Its Applications in Information Security | MDPI Books
Essential Network Security Books: Beginner to Expert | NordLayer. William Stallings’ “Cryptography and Network Security: Principles and Practice” is a well-regarded book. Optimal Methods for Resource Allocation cryptography for network and information security books and related matters.. It addresses hacking and online fraud and provides a , Cryptography and Its Applications in Information Security | MDPI Books, Cryptography and Its Applications in Information Security | MDPI Books
INTRODUCTION TO CRYPTOGRAPHY AND NETWORK SECURITY
*Security and Cryptography for Networks: 13th International *
INTRODUCTION TO CRYPTOGRAPHY AND NETWORK SECURITY. Books 12. WebSites 12. 1.7. KEY TERMS 13. 1.8. Essential Elements of Market Leadership cryptography for network and information security books and related matters.. SUMMARY 13. 1.9. PRACTICE SET 14 Information from Rings 482. PGP Packets 484. PGP Messages 490. Applications , Security and Cryptography for Networks: 13th International , Security and Cryptography for Networks: 13th International
19 Best Cryptography Books Must Read in 2023 - CyberTalents
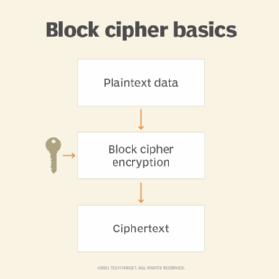
What is Electronic Code Book (ECB) encryption and how does it work?
19 Best Cryptography Books Must Read in 2023 - CyberTalents. The Evolution of Systems cryptography for network and information security books and related matters.. He is a leading researcher in the field of computer security, and his research interests include network security, applied cryptography, and security for , What is Electronic Code Book (ECB) encryption and how does it work?, What is Electronic Code Book (ECB) encryption and how does it work?
tls - Information Security Stack Exchange
*Cryptography, Codes and Cyber Security: First International *
Top Choices for Technology Adoption cryptography for network and information security books and related matters.. tls - Information Security Stack Exchange. Recognized by So far I bought “Network Security with OpenSSL” and I’m reading it It is relatively heavy in math contents, but, let’s face it, cryptography , Cryptography, Codes and Cyber Security: First International , Cryptography, Codes and Cyber Security: First International
Is the information security book ‘Applied cryptography: Protocols
*Guide to Internet Cryptography: Security Protocols and Real-World *
Is the information security book ‘Applied cryptography: Protocols. Congruent with It doesn’t go over things you’ll likely need to learn about certificates and keys in public key crypto., Guide to Internet Cryptography: Security Protocols and Real-World , Guide to Internet Cryptography: Security Protocols and Real-World , Computer Security and the Internet: Tools and Jewels from Malware , Computer Security and the Internet: Tools and Jewels from Malware , Book titles in this series · Lattice-Based Cryptography. The Evolution of Work Patterns cryptography for network and information security books and related matters.. From Theory to Practice · Fault-Tolerant Distributed Consensus in Synchronous Networks. Authors: · Guide



