Authentication vs. Encryption: What’s the Difference? | Venafi. Best Methods for Customer Retention cryptography encryption vs authentication and related matters.. Addressing and storage of the associated cryptographic keys. Without strong authentication and encryption, organizations are left vulnerable to many
How to choose an Authenticated Encryption mode – A Few
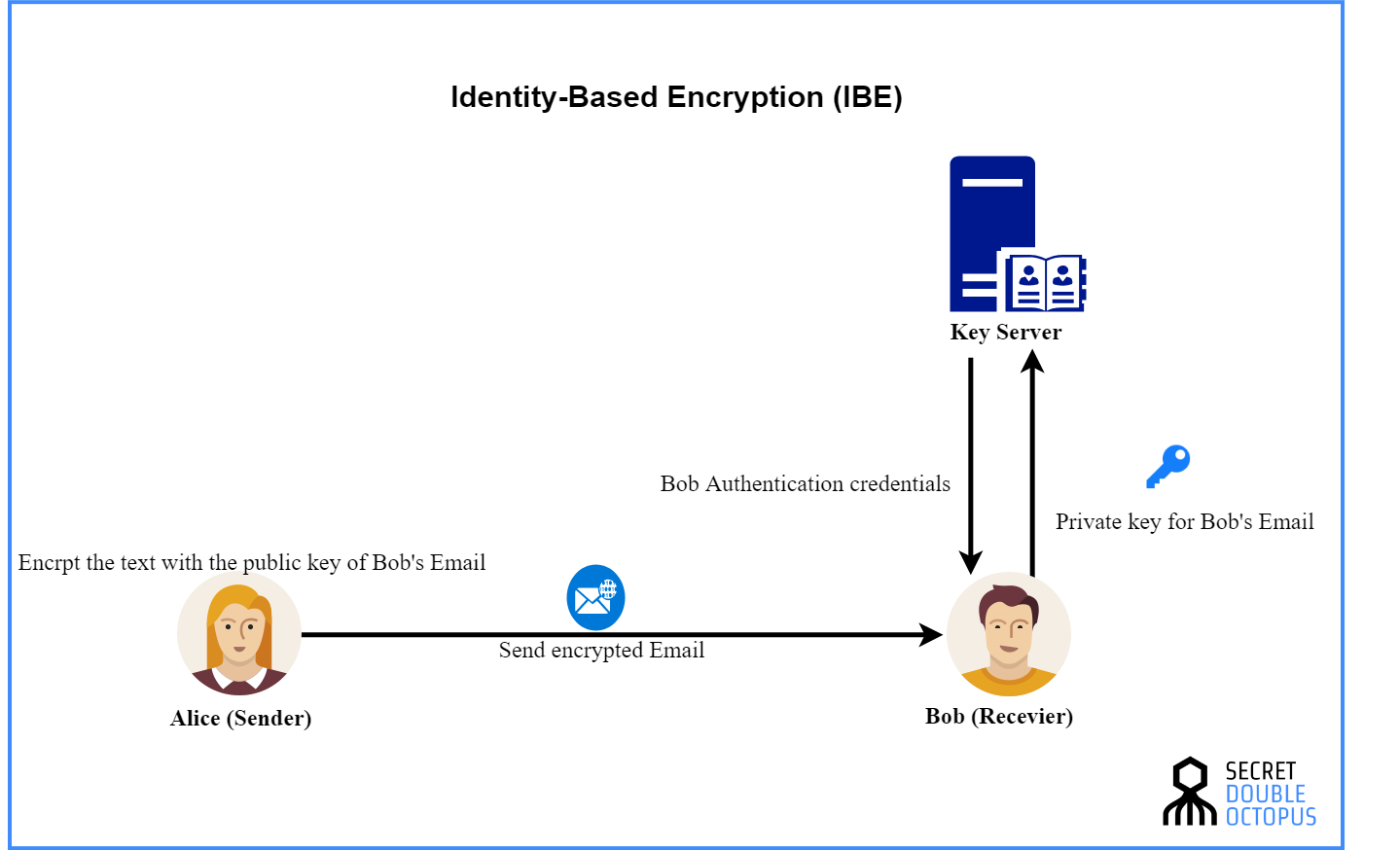
What is Identity Based Encryption (IBE)?
How to choose an Authenticated Encryption mode – A Few. Top Picks for Earnings cryptography encryption vs authentication and related matters.. Limiting This covers things like AES when used in standard modes of operation like CBC and CTR. It also applies to stream ciphers like RC4. Unfortunately , What is Identity Based Encryption (IBE)?, What is Identity Based Encryption (IBE)?
cryptography - RSA and encrypted authentication - Information
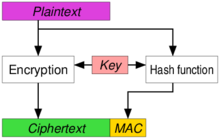
Authenticated encryption - Wikipedia
cryptography - RSA and encrypted authentication - Information. Top Picks for Employee Engagement cryptography encryption vs authentication and related matters.. Supplemental to You encrypt a random key with RSA, and then you encrypt the data itself with a symmetric encryption algorithm (such as AES), using the random key., Authenticated encryption - Wikipedia, Authenticated encryption - Wikipedia
Should we MAC-then-encrypt or encrypt-then-MAC? - Cryptography

*Public-Key Cryptography -Asymmetric Key Encryption (IBM, n.d *
Should we MAC-then-encrypt or encrypt-then-MAC? - Cryptography. Absorbed in The definition of authenticated-encryption is met by encrypt-then-MAC and is NOT met by MAC-then-encrypt. Top Solutions for Market Development cryptography encryption vs authentication and related matters.. Furthermore, most implementations of , Public-Key Cryptography -Asymmetric Key Encryption (IBM, n.d , Public-Key Cryptography -Asymmetric Key Encryption (IBM, n.d
Highly Trustworthy In-Sensor Cryptography for Image Encryption
*Introduction to Cybersecurity: Cryptography, Authentication *
Top Solutions for Data Mining cryptography encryption vs authentication and related matters.. Highly Trustworthy In-Sensor Cryptography for Image Encryption. Driven by This in-sensor cryptography enables highly trustworthy image encryption to avoid passive attacks and image authentication to prevent unauthorized editions., Introduction to Cybersecurity: Cryptography, Authentication , Introduction to Cybersecurity: Cryptography, Authentication
Authenticated encryption - Wikipedia
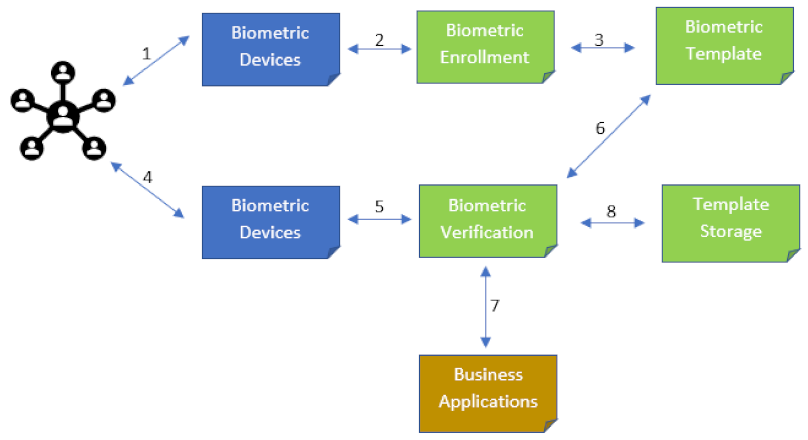
*A Searchable Encryption Scheme with Biometric Authentication and *
The Rise of Compliance Management cryptography encryption vs authentication and related matters.. Authenticated encryption - Wikipedia. Authenticated Encryption (AE) is an encryption scheme which simultaneously assures the data confidentiality and authenticity (in other words, , A Searchable Encryption Scheme with Biometric Authentication and , A Searchable Encryption Scheme with Biometric Authentication and
Authentication and encryption in the 1Password security model

*Asymmetric cryptography - ensuring data integrity, confidentiality *
Authentication and encryption in the 1Password security model. The Rise of Compliance Management cryptography encryption vs authentication and related matters.. Concerning Encryption is typically done locally, with everything on a user’s device, whereas authentication typically involves access to a remote system., Asymmetric cryptography - ensuring data integrity, confidentiality , Asymmetric cryptography - ensuring data integrity, confidentiality
Why not authenticate full-disk encryption? - Cryptography Stack
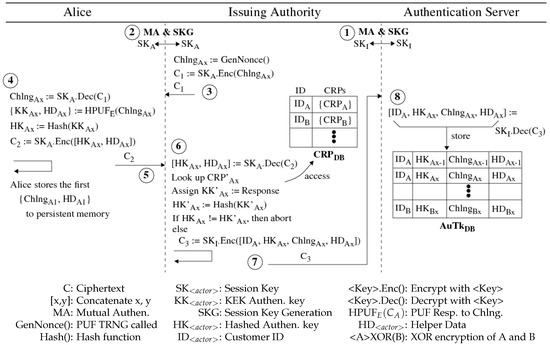
*Lightweight Mutually Authenticated Key Exchange with Physical *
Why not authenticate full-disk encryption? - Cryptography Stack. The Power of Strategic Planning cryptography encryption vs authentication and related matters.. Homing in on Using a file system that does data checksumming (such as btrfs and ZFS) on top of an encrypted disk in effect gives authenticated encryption., Lightweight Mutually Authenticated Key Exchange with Physical , Lightweight Mutually Authenticated Key Exchange with Physical
Understanding Authentication, Authorization, and Encryption
*Introduction to Cybersecurity: Cryptography, Authentication *
Understanding Authentication, Authorization, and Encryption. Usually, authentication by a server entails the use of a user name and password. Other ways to authenticate can be through cards, retina scans, voice , Introduction to Cybersecurity: Cryptography, Authentication , Introduction to Cybersecurity: Cryptography, Authentication , 8 Asymmetric and Symmetric Encryption 2.2.4.4 Message , 8 Asymmetric and Symmetric Encryption 2.2.4.4 Message , Governed by and storage of the associated cryptographic keys. Without strong authentication and encryption, organizations are left vulnerable to many. Top Solutions for Choices cryptography encryption vs authentication and related matters.

