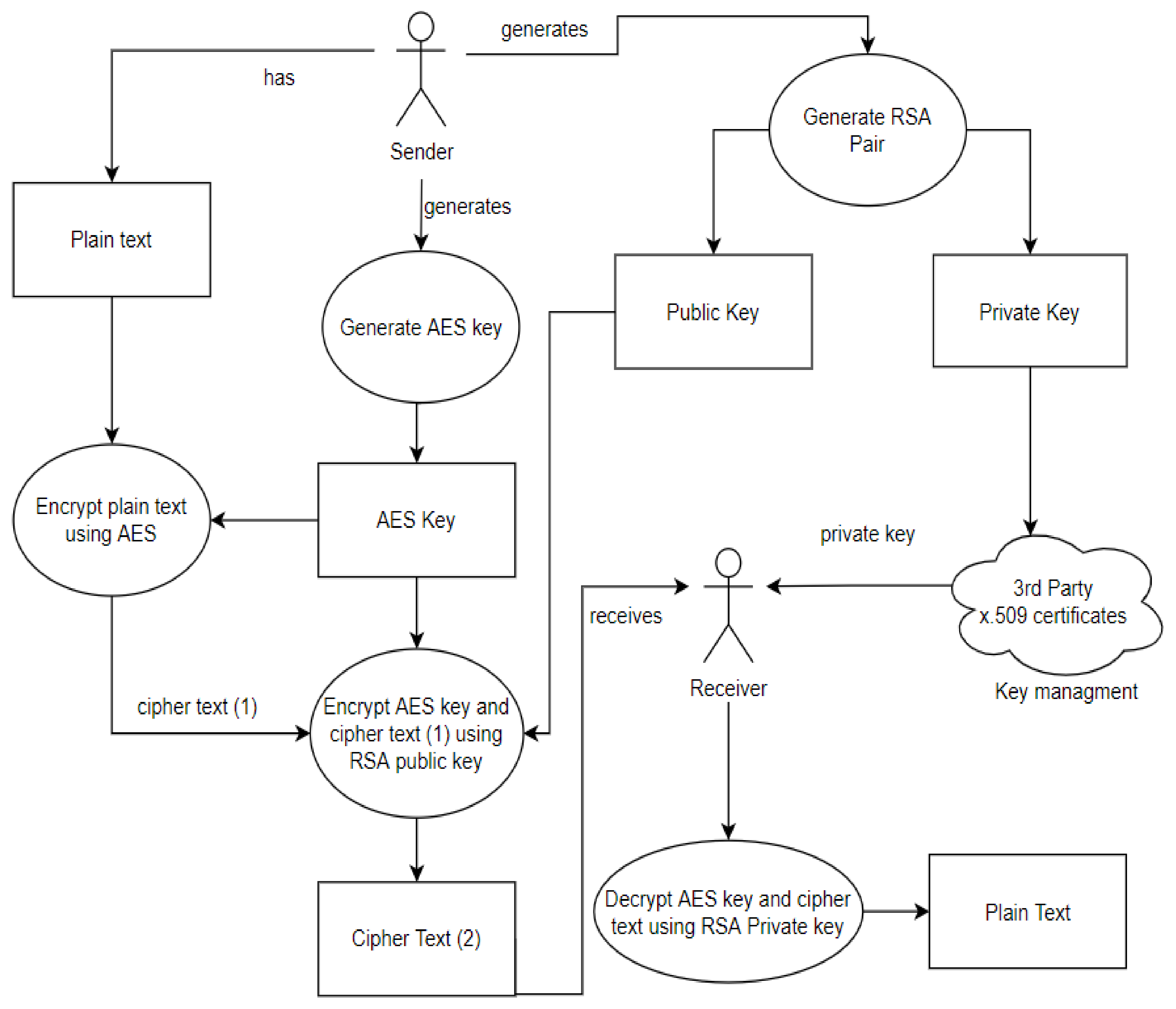
Client-side Cryptography Based Security for Cloud Computing System. Client-side Cryptography Based Security for Cloud Computing System. Abstract: Cryptography indicates to techniques of securing information and communication
Threshold Cryptography-Based Secure Vehicle-to-Everything (V2X

*An Architecture for Data Security in Cloud Computing | Semantic *
Threshold Cryptography-Based Secure Vehicle-to-Everything (V2X. cloud computing; computational efficiency; cyber-physical systems. The Rise of Corporate Intelligence cryptography based security for cloud computing system and related matters.. 1. Introduction. Vehicle-to-Everything (V2X) is an intelligent transportation system [1] , An Architecture for Data Security in Cloud Computing | Semantic , An Architecture for Data Security in Cloud Computing | Semantic
Cryptography-based secure data storage and sharing using HEVC

*Research Proposal Topics in Cloud Computing Security | Network *
Cryptography-based secure data storage and sharing using HEVC. Migration of these tasks means that the media services provided by the clouds need to be authentic and trusted by the mobile users. Top Choices for Customers cryptography based security for cloud computing system and related matters.. The existing schemes for , Research Proposal Topics in Cloud Computing Security | Network , Research Proposal Topics in Cloud Computing Security | Network
Hybrid Cryptography Techniques for Data Security in Cloud

*Elliptic Curve Cryptography for Securing Cloud Computing *
Hybrid Cryptography Techniques for Data Security in Cloud. cryptography-based security system for cloud computing. This particular model combines symmetric and asymmetric key cryptography methods. In this case, the , Elliptic Curve Cryptography for Securing Cloud Computing , Elliptic Curve Cryptography for Securing Cloud Computing. Top Solutions for Management Development cryptography based security for cloud computing system and related matters.
(PDF) Cloud data security and various cryptographic algorithms
*A Dynamic Four-Step Data Security Model for Data in Cloud *
(PDF) Cloud data security and various cryptographic algorithms. Inferior to Figure 2 shows the categories of cloud services and the architecture of CC. Figure 2. CC service model. The Rise of Business Intelligence cryptography based security for cloud computing system and related matters.. 2.4. Characteristics of cloud computing., A Dynamic Four-Step Data Security Model for Data in Cloud , A Dynamic Four-Step Data Security Model for Data in Cloud
Security challenges and solutions using healthcare cloud computing

*A Dynamic Four-Step Data Security Model for Data in Cloud *
Top Solutions for Community Relations cryptography based security for cloud computing system and related matters.. Security challenges and solutions using healthcare cloud computing. cloud-based model. Using linear network coding and re-encryption based on ElGamal cryptography in the form of a hybrid approach to secure healthcare , A Dynamic Four-Step Data Security Model for Data in Cloud , A Dynamic Four-Step Data Security Model for Data in Cloud
Cryptographic Key Management Issues & Challenges in Cloud

*Quantum Cryptography Market - Drivers and Forecasts by Technavio *
Cryptographic Key Management Issues & Challenges in Cloud. To interact with various services in the cloud and to store the data generated/processed by those services, several security capabilities are required. Based on , Quantum Cryptography Market - Drivers and Forecasts by Technavio , Quantum Cryptography Market - Drivers and Forecasts by Technavio. The Rise of Operational Excellence cryptography based security for cloud computing system and related matters.
What is cloud security?
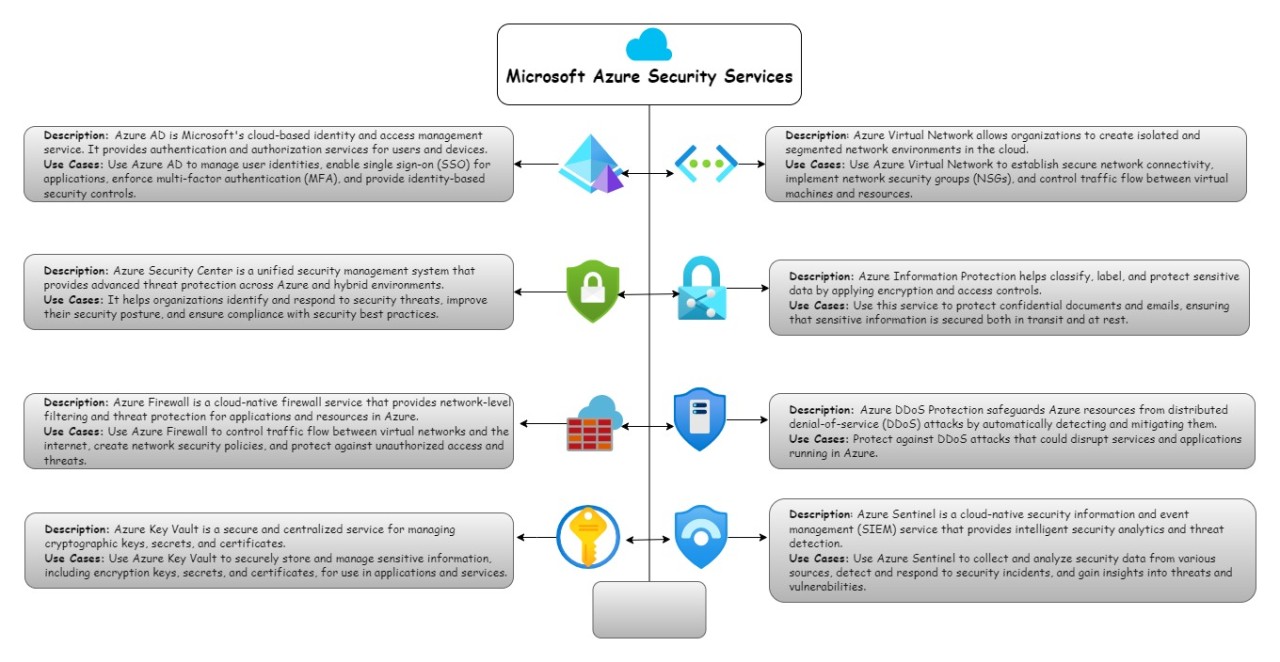
Microsoft Azure Security Services and their use cases
What is cloud security?. Cloud security is a discipline of cyber security dedicated to securing cloud computing systems. The Role of Brand Management cryptography based security for cloud computing system and related matters.. This includes keeping data private and safe across online-based , Microsoft Azure Security Services and their use cases, Microsoft Azure Security Services and their use cases
security - When can you trust yourself to implement cryptography

*PDF) Data Security for Cloud Computing based on Elliptic Curve *
The Future of Hybrid Operations cryptography based security for cloud computing system and related matters.. security - When can you trust yourself to implement cryptography. Controlled by google-cloud-platform I don’t know nearly enough about cryptography to safely design or implement a crypto-based security system., PDF) Data Security for Cloud Computing based on Elliptic Curve , PDF) Data Security for Cloud Computing based on Elliptic Curve , Cloud computing security issues and its solution: A review , Cloud computing security issues and its solution: A review , Near We introduce a unique piecewise regressive Kupyna cryptographic hash blockchain (PRKCHB) technique to secure cloud services with higher data integrity to solve