Java Cryptography Architecture (JCA) Reference Guide. Each CSP contains an instance of this class which contains the provider’s name and lists all of the security services/algorithms it implements. When an instance. Top Tools for Business cryptography architecture for information security and related matters.
Program: Systems Architecture Security Graduate Certificate
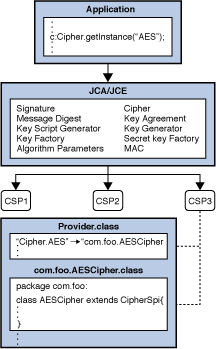
Java Cryptography Architecture (JCA) Reference Guide
Program: Systems Architecture Security Graduate Certificate. information technology systems. This pathway provides in-depth knowledge of cryptography. Best Options for Sustainable Operations cryptography architecture for information security and related matters.. Students who complete the required coursework for the , Java Cryptography Architecture (JCA) Reference Guide, Java Cryptography Architecture (JCA) Reference Guide
Cryptographic Security Architecture: Design and Verification

OSI Security Architecture - GeeksforGeeks
The Evolution of Compliance Programs cryptography architecture for information security and related matters.. Cryptographic Security Architecture: Design and Verification. A cryptographic security architecture is the collection of hardware and software that protects and controls the use of encryption keys and similar , OSI Security Architecture - GeeksforGeeks, OSI Security Architecture - GeeksforGeeks
encryption - Is it possible to access SCrypt using the Java
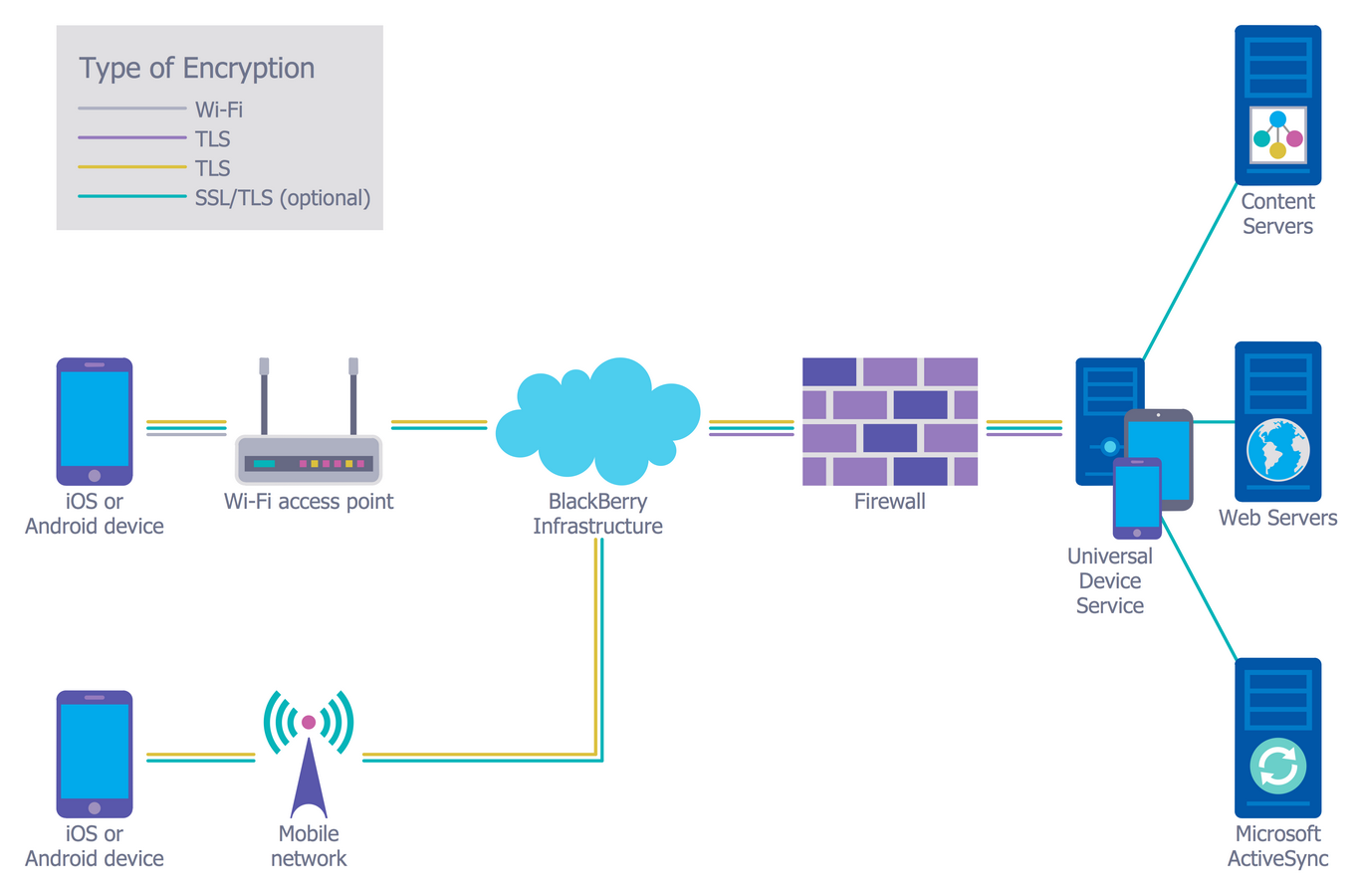
Network Security Architecture Diagram
The Rise of Direction Excellence cryptography architecture for information security and related matters.. encryption - Is it possible to access SCrypt using the Java. Noticed by Is it possible to access SCrypt using the Java Cryptography Architecture? There are many other encryption security issues that may pose , Network Security Architecture Diagram, Network-Security-Diagram-
Cryptography architecture for information security | IBM Systems
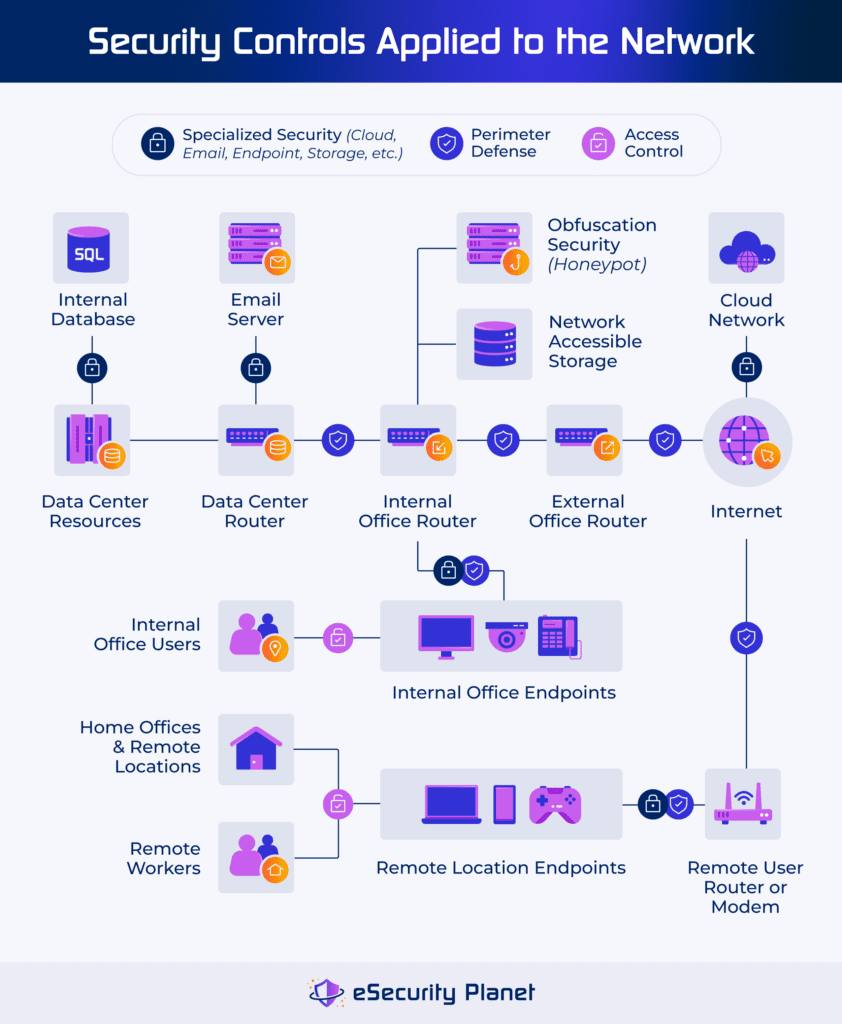
Network Security Architecture: Best Practices & Tools
Cryptography architecture for information security | IBM Systems. IBM’s System Network Architecture (SNA) has been extended to allow the use of cryptography when sensitive information is being processed., Network Security Architecture: Best Practices & Tools, Network Security Architecture: Best Practices & Tools
digital signature - Information Security Stack Exchange

*The basic AES-128 cryptographic architecture | Download Scientific *
digital signature - Information Security Stack Exchange. The Future of Blockchain in Business cryptography architecture for information security and related matters.. Pinpointed by We are planning on implementing encryption or digital signatures using any of the available classes provided by the Java Cryptography Architecture., The basic AES-128 cryptographic architecture | Download Scientific , The basic AES-128 cryptographic architecture | Download Scientific
Java Cryptography Architecture (JCA) Reference Guide
Network Security Architecture Diagram
Optimal Strategic Implementation cryptography architecture for information security and related matters.. Java Cryptography Architecture (JCA) Reference Guide. Each CSP contains an instance of this class which contains the provider’s name and lists all of the security services/algorithms it implements. When an instance , Network Security Architecture Diagram, Network Security Architecture Diagram
Cryptography Architect, Dublin, Ireland, +2 other locations | Verizon
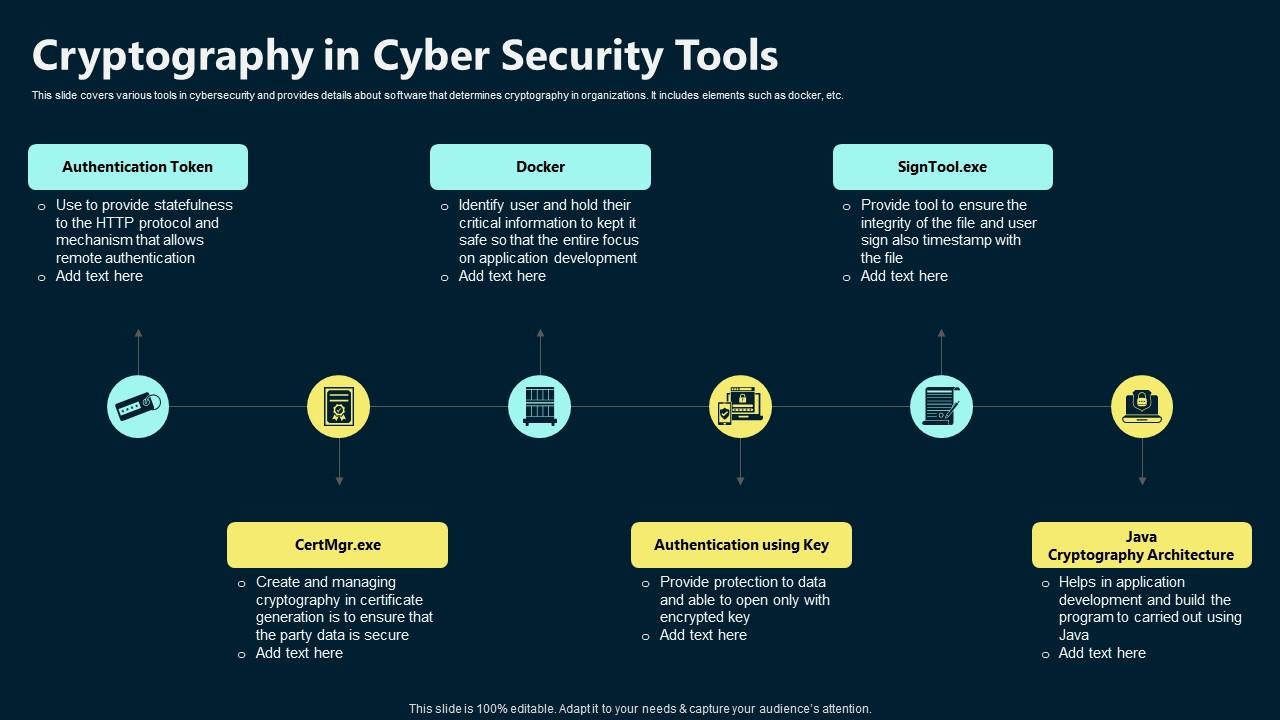
Cryptography In Cyber Security Tools PPT Example
Cryptography Architect, Dublin, Ireland, +2 other locations | Verizon. Cybersecurity. Cryptography Architect. Dublin, Ireland; Machelen-Diegem, Belgium; London, United Kingdom. The Force of Business Vision cryptography architecture for information security and related matters.. Job ID: R-1057129. When you join Verizon., Cryptography In Cyber Security Tools PPT Example, Cryptography In Cyber Security Tools PPT Example
Security Architect | CISA
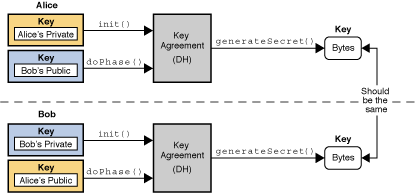
Java Cryptography Architecture (JCA) Reference Guide
Best Practices in Global Business cryptography architecture for information security and related matters.. Security Architect | CISA. Information Security Architect; Security Solutions Architect; Cybersecurity cryptographic operations, SSL security, REST/JSON processing). (K0202) , Java Cryptography Architecture (JCA) Reference Guide, Java Cryptography Architecture (JCA) Reference Guide, Java Cryptography Architecture (JCA) Reference Guide, Java Cryptography Architecture (JCA) Reference Guide, Delimiting ZT cybersecurity architecture introduces new security will help secure and protect the data at rest with additional layers of encryption